In the last issue of Cyber Series, we looked at Penetration testing for regulatory compliance and provided a checklist for organisations that are commissioning a penetration test. The final item on that list is:
Understand the deliverables and how the output aligns to internal processes and risk management:
- Does the report provide business context that can be understood and aligned to existing processes to help aid risk reduction?
- The deliverables must answer the questions, “what?,” “so what?,” and “now what?”

This week, we look at the “now what?" in more detail.
Please note: In an ideal world there would be an existing vulnerability management policy with supporting processes outlining how to manage and process any findings, but in the real-world things may differ somewhat….
After a penetration test, a proper clean up should take place, including the removal of any tooling and/or accounts used during the testing – though this should be validated. Often this involves activities by both the tester and the client organisation, but these are not always done.Taking a moment to check that the activities have been completed is important.
Despite what some may believe, the real value of a penetration test (pen test) lies in the wider activities that should occur after the test has been completed. These activities can be overlooked, and so an opportunity to extract extra value from the pen test is missed.
The broader outcomes of an organisation’s penetration test could include:
- Defining the mitigating actions and activities to address identified vulnerabilities.
- Confirming the effective implementation of security controls.
- Using its findings to set KPIs at internal meetings across the wider organisation.
- Identifying the wider issues or concerns within the business, including underlying factors that could be contributing to the findings of the pen test.
- Providing an input into the wider asset management strategy, including contributing to planning for the decommissioning of outmoded or legacy technology.
An effective process will examine the penetration test report in detail and develop a thorough understanding of each of the findings. (As discussed previously, the ability to speak to the tester can make all the difference and can be useful for the internal IT and security team(s).) The report will provide a rating for the findings, however a risk assessment driven by the organisation’s own knowledge and understanding of their own business should be conducted.
A robust risk assessment requires detailed knowledge of an organisation’s key processes, technologies, and operations. A “high” rated vulnerability in a non-critical system may present lower risk than a “medium” rated finding in a business-critical system. Having conducted the risk assessment and placed the findings within the critically important context of the business, appropriate plans for remediation should be agreed and shared with the relevant stakeholders.
With a very broad potential audience that includes everyone from members of the technical teams to members of the board, appropriately worded internal reports are needed. Transparent communication fosters accountability and ensures that everyone understands their role in maintaining security. Upwards and proactive communication is now expected from mature cyber security teams. An established change management process will be required and, as per good practice, appropriate planning and testing conducted.
Remediation activity may involve applying security patches, software updates, or configuration changes to vulnerable systems, as well as implementing additional security controls to mitigate the risk of exploitation. This will reduce your exposure to cyber threats and strengthen your overall security posture. The frequently overlooked part here is that changing the configuration within a system, device or application could be a way of addressing the root cause of multiple vulnerabilities, an act that forms part of another vital control, i.e., that of system hardening.
It is imperative that penetration tests are carried out periodically for two reasons:
- to assess the effectiveness of the implemented security measures and to detect new vulnerabilities; and
- to ensure that existing measures are still sufficient after significant changes within the technology landscape.
Regular penetration testing helps to identify and address security weaknesses proactively, enabling you to stay ahead of potential cyber threats and maintain a strong security posture over time.
Making sure existing documentation is reviewed and updated to ensure they adequately address lessons learned from the penetration test and the latest security threats is key. This may involve revising existing policies, developing new ones where necessary, and ensuring that everyone in your organisation is aware of – and complies with – your security policies and procedures. (An example the need to review internal development practices should a penetration test detect a high number of vulnerabilities within an internally developed application.)
In addition to remediation efforts, best practice dictates reviewing and strengthening your wider security controls on an ongoing basis. This may involve enhancing network security measures, such as firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS), as well as implementing robust authentication mechanisms and access controls.
It is essential that you document:
- all penetration test findings;
- the implemented corrective actions; and
- additional security measures taken.
This documentation, when regularly updated, serves as a record of your organisation’s security activities, and can be used for compliance purposes, internal audits, and for establishing continuity in your IT and cyber security teams (regardless of personnel changes).
Finally, use the results of your penetration tests to establish a process for continuous improvement in cyber security. A penetration test is not a ‘one and done’ exercise, but part of the continuous assessment and series of activities to drive improvement in your cyber security posture.

Cyber Risk
We bring the best of our collective experience, energy and creative power to fiercely safeguard our clients and fortify their communities.
Insights

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
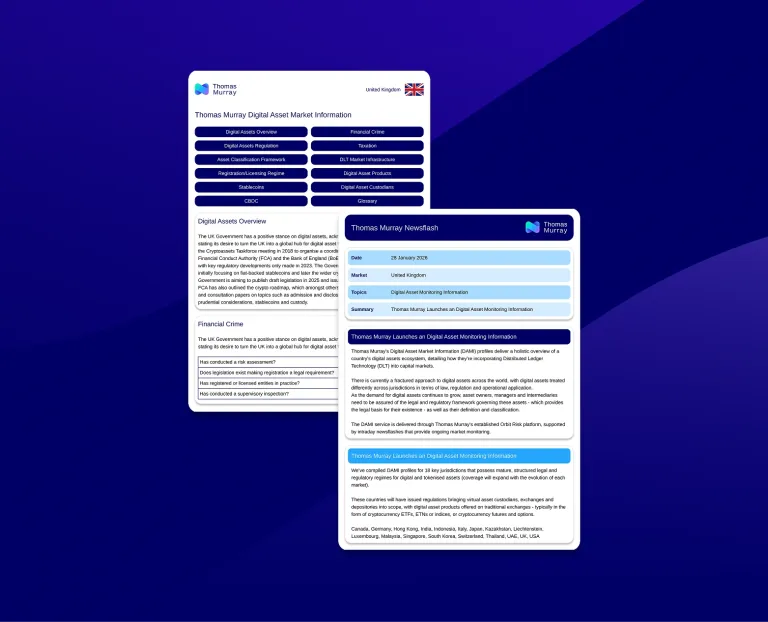
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.

How Private Equity Hackers Choose Their Targets
Private equity firms sit at the intersection of high-value financial transactions, sensitive deal data, and an expanding portfolio of technology heavy portfolio companies – and it’s this combination that makes PE an attractive target for cyberthreat actors.

