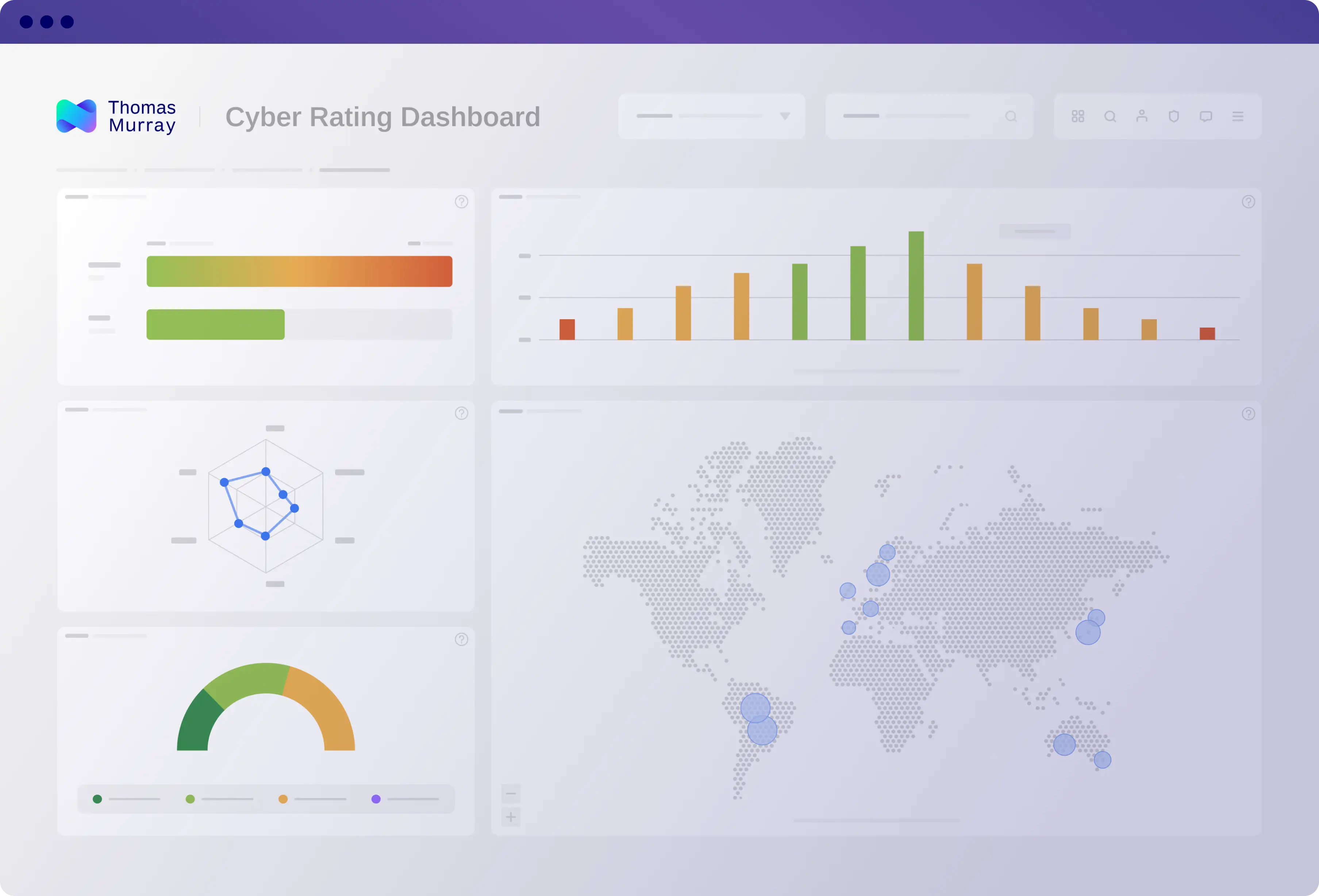
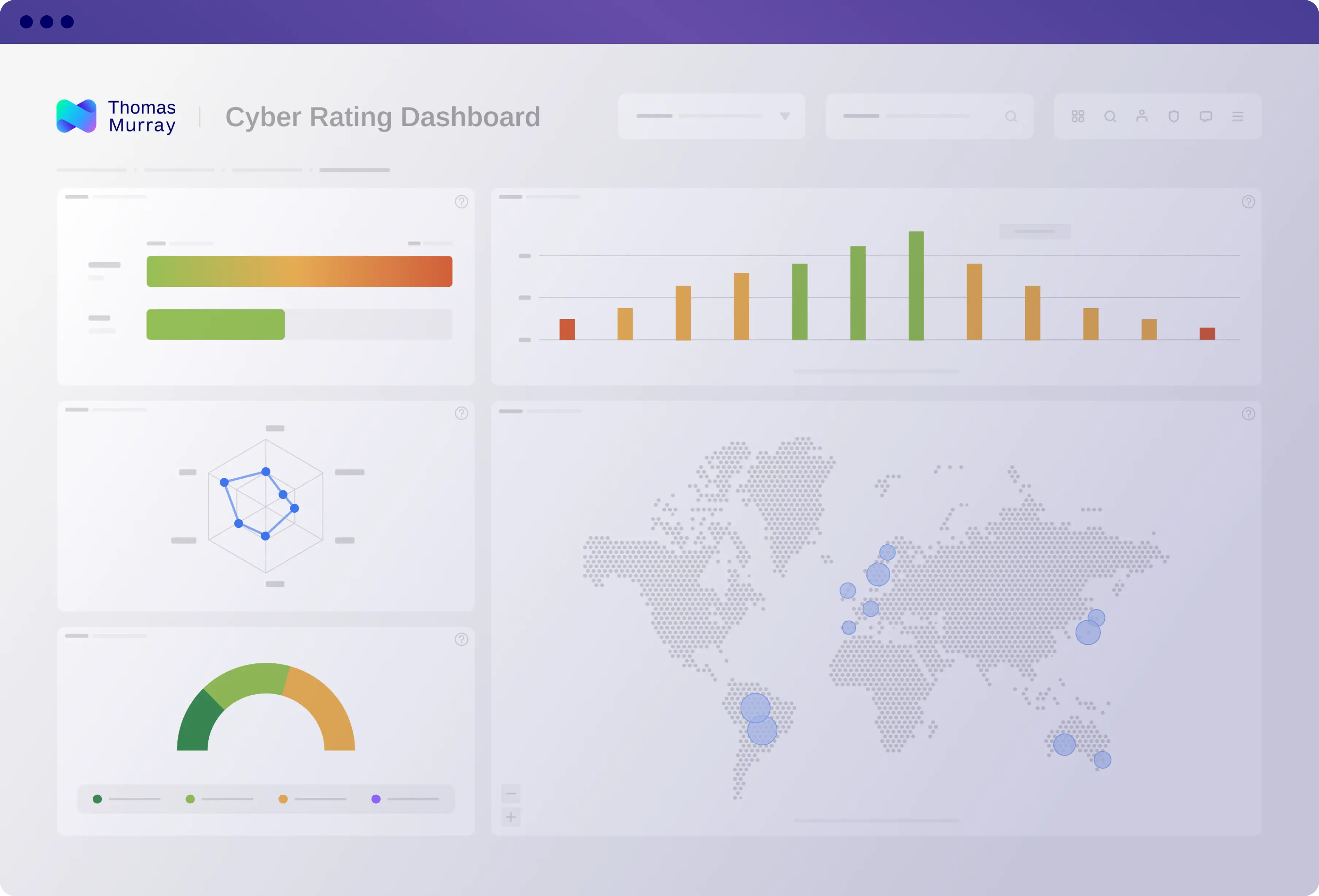
See what your hackers see

Data and infrastructure breaches

Discover infrastructure and data breaches; remediate potential issues to mitigate the breach impact; and protect your clients' data and reputations.

Mail security

Check mail servers for potential issues to prevent attackers from impersonating members of your organisation or using its email infrastructure to target others.
Server configuration

Stop attackers from targeting and exploiting vulnerabilities and potential security issues by detecting the various publicly accessible services running on your servers.
HTTP and HTTPS

Prevent hackers from breaking into your organisation's resources by scanning for issues in your websites and web applications.

SSL and TLS

Identify the common configuration issues in the complex SSL/TLS protocols that can allow attackers access to a compromised SSL/TLS certificate.
Domain name system (DNS)

Monitor easily unnoticed inconsistencies in DNS configuration and synchronisation before they affect your security, performance, and reputation.
How it works

Provide Thomas Murray with your root domain

Discover your exposed attack surface
Continuously monitor the risks and vulnerabilities within your network

Review your ratings, analytics, and actionable remediation data
Sector-by-sector benchmarking
Compare your company’s security posture to that of others in your industry, or assess how your critical third parties’ 0 to 1,000 ratings compare to their competitors, with bespoke industry benchmarks:

Bank

Asset managers

Asset owners

Market infrastructures

Government and public sector

Healthcare

Telecommunications

Manufacturing and logistics

Consultancies

Retail and customer

Technology

Other corporate sectors
Security Ratings Solutions: The 2023 Comparison
There are a lot of security ratings and third-party risk management solutions out there – choosing the right partner is a challenge. We've taken a step back to help you compare Thomas Murray’s market-leading solution, Orbit Security, with other well-known providers in the market.
Capabilities
Headquarters
Founded / Product Launched
Security rating scale
Orbit Security
Capabilities
- Security Ratings
- Third-Party Risk Management
- Cyber Advisory
- Incident Response
- Cyber Threat Simulation
- eDiscovery
Headquarters
London
Founded / Product Launched
1994 / 2021
Security rating scale
0-1000 for overall, domain and sub-domain level ratings
BitSight
Capabilities
- Security Ratings
- Third-Party Risk Management
Headquarters
Boston
Founded / Product Launched
2011 / 2013
Security rating scale
0-950 for overall rating
SecurityScorecard
Capabilities
- Security Ratings
- Third-Party Risk Management
- Incident Response
- Cyber Threat Simulation
Headquarters
New York
Founded / Product Launched
2013 / 2014
Security rating scale
A-F for overall rating, with A-F and 0-100 scale for individual risks

Have any questions?
Have any questions?
We safeguard clients and their communities
Insights

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
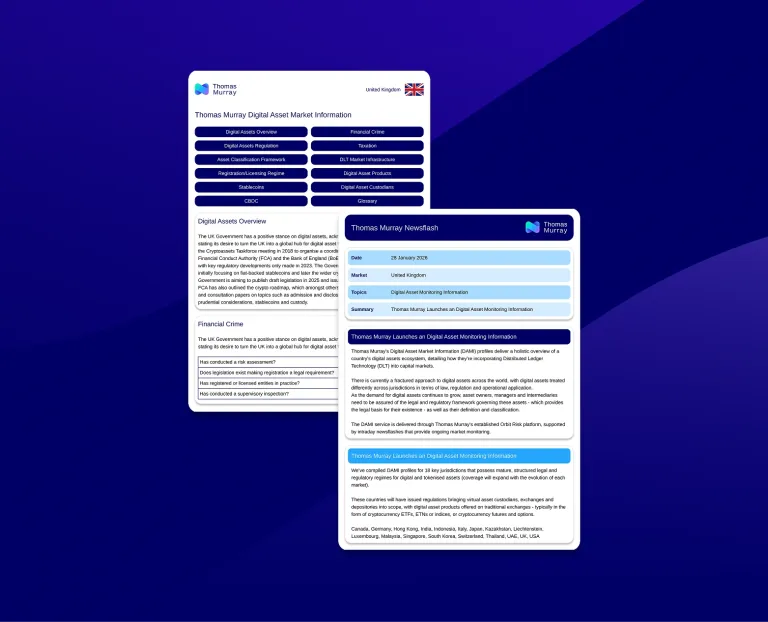
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.

How Private Equity Hackers Choose Their Targets
Private equity firms sit at the intersection of high-value financial transactions, sensitive deal data, and an expanding portfolio of technology heavy portfolio companies – and it’s this combination that makes PE an attractive target for cyberthreat actors.
Contact an expert