Conduct a deep assessment
Use Orbit Diligence to access Thomas Murray’s library of digitised IT security questionnaires, with auto-scoring, in-platform vendor communication, document storage and reporting. Automate the issuance of questionnaires and leverage Orbit’s intuitive workflows to save both you and your third parties time and manual effort.
Take action
Escalate with a potentially high-risk third-party by providing full access to its security rating and threat intelligence assessment, automatically flagging high-impact remediation so that their IT security team can begin improving their score from day one. Thomas Murray’s cyber security analysts will engage with your third parties to help them understand, contextualise and implement their assessment – you only need to make the introduction.

Have any questions?
Have any questions?
Simplify your vendor risk

Automated
By combining automated “external” security ratings and digitised “internal” IT security questionnaire, you can establish a sophisticated monitoring programme without adding to budget or headcount.

Centralised
Orbit is the only solution which combines expert security ratings with deep due diligence capacities, meaning that you can centralise your third-party risk management on a single, easy-to-use platform.

Compliant
Orbit is designed to help lean teams meet stringent regulatory requirements. We help clients achieve compliance by demonstrating a proactive approach with deep assessments, tailored reporting and audit trails.
We safeguard clients and their communities
Manage
Attack surface discovery
- Automated discovery of digital assets.
- Eliminate false positives.
- Monitor for changes.
Security ratings
- Organisation security ratings.
- Domain security ratings.
- Benchmarking.
Attack surface reduction
- Breaches.
- Vulnerabilities.
- Misconfigurations.
Monitor
Reporting and benchmarking
- C-Suite reporting.
- Alerts and automated reports.
- Custom competitor analysis.
Enquiries and improvements
- Live enquiries tool.
- Access to expert analysts.
- Track organisation and domain scores.
Integration
- APIs.
Oversight
- Accounts and permissions.
- Historical scores.
- Account security.
Escalate
Third parties
- Provide free access for remediation.
- Monitor changes.
IT security questionnaires
- Issue and analyse.
- Manage and monitor.
- Assess and remediate.
Vendor due diligence and selection
- Standard and custom questionnaires.
- Track, report and benchmark.
Insights

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
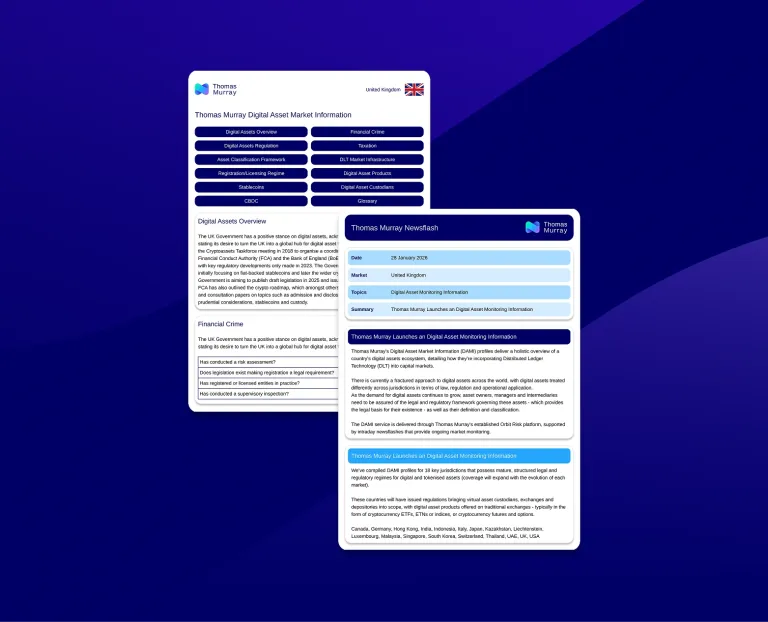
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.

How Private Equity Hackers Choose Their Targets
Private equity firms sit at the intersection of high-value financial transactions, sensitive deal data, and an expanding portfolio of technology heavy portfolio companies – and it’s this combination that makes PE an attractive target for cyberthreat actors.
Contact an expert