Manage
Attack Surface Discovery
- Automated discovery of digital assets.
- Eliminate false positives.
- Monitor for changes.
Security Ratings
- Organisation security ratings.
- Domain security ratings.
- Benchmarking.
Attack Surface Reduction
- Breaches.
- Vulnerabilities.
- Misconfigurations.
Monitor
Reporting and Benchmarking
- C-Suite reporting.
- Alerts and Automated reports.
- Custom competitor analysis.
Enquiries and Improvements
- Live enquiries tool.
- Access to expert analysts.
- Track organisation and domain scores.
Integration
- APIs.
Oversight
- Accounts and permissions.
- Historical scores.
- Account security.
Escalate
Third Parties
- Provide free access for remediation.
- Monitor changes.
IT Security Questionnaires
- Issue and Analyse.
- Manage and Monitor.
- Assess and Remediate.
Vendor Due Diligence and Selection
- Standard and custom questionnaires.
- Track, report and benchmark.

Speak with
an Expert
Speak with
an Expert
Manage your third parties
Gain visibility over your third parties with accurate, automated attack surface discovery, actionable security ratings and like-for-like peer comparison.
Attack surface discovery
Automated discovery of digital assets
Orbit Cyber Risk’s powerful Machine-Learning algorithm accurately and automatically discovers your public-facing IT infrastructure.
- ML algorithm automates the discovery process
- Continuously monitors for domains added or taken offline
- Identifies absolute global exposure, not just infrastructure managed by local IT team
- Pinpoint’s location of digital assets globally
Eliminate false positives
Attack surface discovery module is designed to eliminate false positives, accurately identifying the digital assets an organisation manages and is exposed to.
- Minimal manual intervention required
- Highly accurate for identifying each of your underlying domains
- Robust, absolute methodology, not liable to user manipulation
Monitor for changes
ttack surface discovery module is designed to eliminate false positives, accurately identifying the digital assets an organisation manages and is exposed to.
- Automatically monitors for new domains
- Alerts users when changes occur
- Updated continuously
Security Ratings
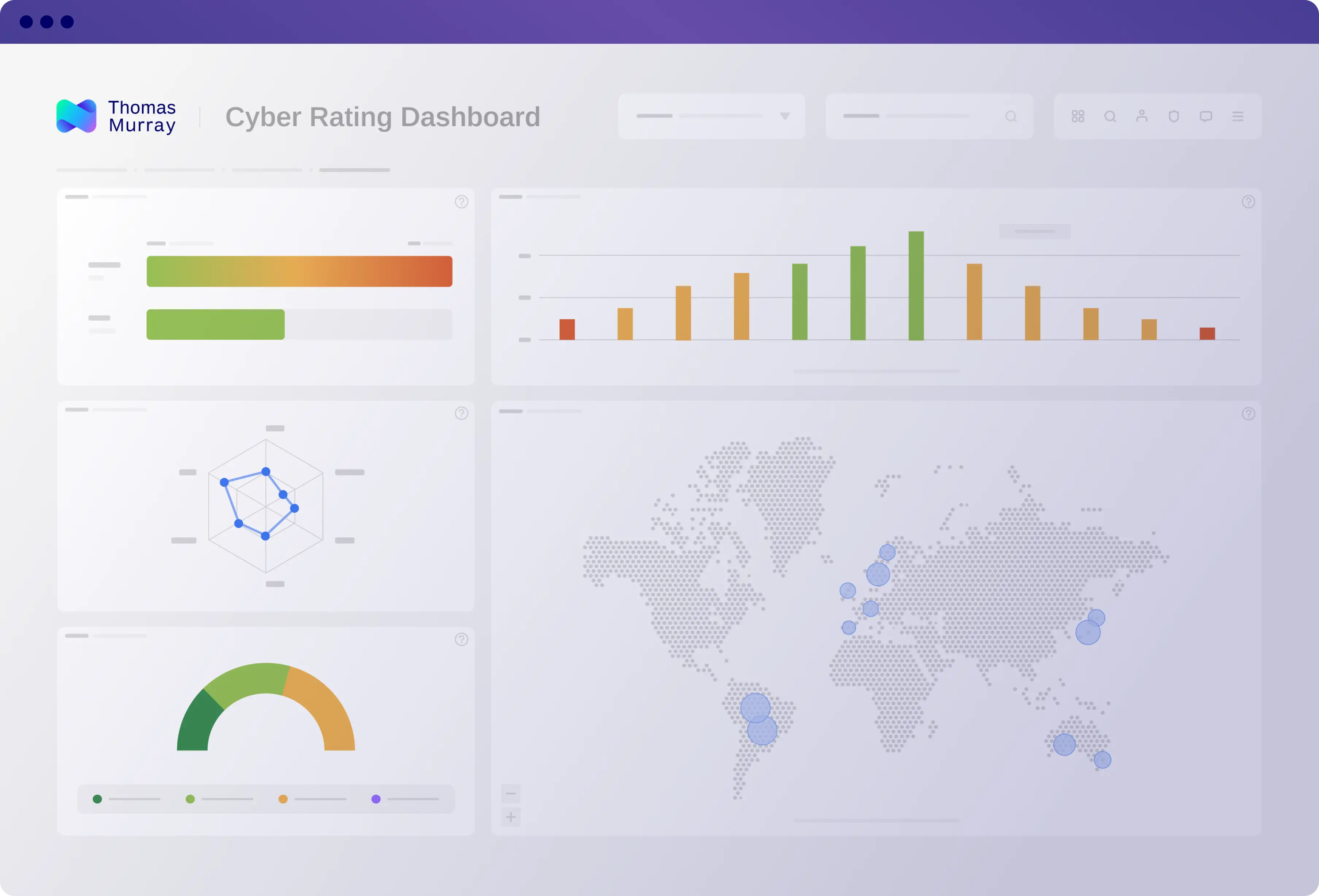
Organisation security ratings
Orbit Cyber Risk ratings provide continuous, objective analysis of your network. Our security ratings are based on Thomas Murray’s proprietary methodology, as well as analysis of open-sources and high-quality third-party data feeds.
- Organisation security rating from 0-1000
- Analyses 10,000+ data points across six risk categories
- Identifies breaches, vulnerabilities and misconfigurations across your attack surface
- Updated continuously
Domain security ratings
Visualise risk at a domain and sub-domain level, with individual ratings for every digital asset in your footprint. Explore the underlying issues, toggle according to the highest risk to focus remediation.
- Security ratings for every underlying digital asset, from 0-1000
- Drill into underlying risks, prioritised by impact
- Access detailed explanations and remediation advice
Benchmarking
Orbit Cyber Risk benchmarks your organisation against its peers, giving absolute security ratings a real-world perspective.
- Compare your organisation to every other major group in your sector
- Benchmark against Orbit’s ‘Global’ universe
- Custom benchmark against named competitors
Risks
Breaches
iscover breaches in your network to prevent attacks which could lead to data loss, operational disruption, financial loss or reputational damage.
- Continuously monitor for infrastructure breaches including Malware, Phishing or Port Scanning.
- Identify when data breaches have occurred, such as employee email addresses and passwords.
- Take action to prevent attacks and build resilience.
Vulnerabilities
Discover vulnerabilities running on your domains that could be exploited by malicious actors.
- Identify publicly accessible services with known vulnerabilities that do not need to be exposed.
- Scan for c.10,000 known issues and vulnerabilities.
- Each vulnerability has an impact rating, helping you determine its criticality.
Misconfigurations
Continuous information about misconfigurations observed in your network, allowing you to remediate potential operational and security issues.
- Check for misconfigurations in your network such as issues in your DNS setup, TLS or HTTPS configuration.
- Protect your security, performance, and reputation.
- Each misconfiguration has an impact rating, helping you determine its criticality.
Monitor
Get alerts directly into your inbox, create tailored benchmarks, and report with confidence to management in a language they understand. Manage accounts with confidence and raise enquiries directly with our expert analysts.
Reporting and Benchmarking
Executive Reporting
Access tailored management reporting suite for boards, regulators, risk and compliance and IT Security.
- Reporting with scores, history, benchmarks and underlying risks.
- Filter based on multiple categories.
- Generate customised reporting.
- Export to PDF
Email Notifications
Get real-time alerts and reporting on your portfolio directly into your inbox, with custom tiggers and recipients.
- Default notifications when third-party scores drop.
- Set custom notifications to ensure oversight at all times.
- Customise audience, risk triggers and timing.
- Set regular, bespoke reports summarising risks.
Custom Competitor Analysis
Create custom benchmarks of direct peers and competitors.
- Default benchmarks against peers and ‘Global’ universe of companies.
- Customise benchmarks to include names competitors, for vendor assessment and selection.
- rovide management with comparative, as well as absolute, cyber risk performance in language they understand.
Enquiries and Improvements
Live enquiries tool
Complement the tool’s continuous security analysis and intuitive dashboards by raising enquiries with our expert team.
- Scan every vendor for c.10,000 known issues and vulnerabilities.
- Identify known vulnerabilities that do not need to be exposed.
- Every risk is given an explanation and impact rating. ,
- Raise granular or high-level queries to escalate with a third-party or request more information
Access to expert analysts
Access our team to escalate with third parties, request remediation advice, risk quantification or any other queries.
- Request any third-party is given 30-day full, free access to their report.
- All queries responded to be expert analysts.
- Query anything from risk impact to remediation tips and likely score improvements.
- Reduce your expose with the help of industry experts.
Track organisation and domain scores
See how your portfolio’s score changes over time, as well as every underlying domain.
- Chart score changes over time and monitor for high-risk vendors.
- Provide access to companies in your portfolio and see the impact of their remediations in real time.
- Demonstrate to management the impact of their investment.
Oversight and Operations
Accounts and Permissions
Share access with InfoSec and management colleagues across departments and offices and provide access to high-risk third parties.
- Get real-time information, security ratings and remediation steps via our API.
- Integrate existing risk feeds into Thomas Murray’s platform.
- Integrate your risk analysis into a single platform for ease of use and holistic oversight.
Historical Performance
See your organisation’s security performance at any point in history.
- Provide access to colleagues in your team and across departments.
- Allocate permissions and track account usage.
- Add or remove users easily.
- Request 30-day full, free access to high-risk third parties.
Account Security
Ensure account and data security with permissions, sensitive data redaction and robust platform security.
- View your full analysis from any historical point in time.
- See how remediations have impacted risk profile over time.
- Demonstrate reduced attack surface to management.
- Report on any previous point in time.
- Manage SSO permissions with other Thomas Murray platforms and products.
- Breached sensitive data is redacted and carefully managed.
- Thomas Murray’s platform and staff adhere to the highest security standard.
Escalate with third parties according to your risk framework
Provide third parties free and full access to the Cyber Risk dashboard to remediate key issues; issue questionnaires to any third-party to find out more about their internal security- controls, procedures, frequency of testing, details of recent breaches and much more.
Third Parties
Provide free access for remediation
Provide third parties with full, free access to their assessment for 30 days.
- Request 30-day free access for any third-party.
- Request that they engage with the platform to remediate key risks.
- Highest areas of concern or refer to Thomas Murray’s analysts.
Monitor changes
See your clients’, suppliers’ and other counterparties’ scores improve every week, demonstrably reducing supply chain risk.
- Track scores across your portfolio.
- Receive alerts whenever scores drop significantly, according to your risk appetite.
- Maintain a low-risk portfolio and escalate with high-risk providers.
IT Security Questionnaires
Issue and analyse
Escalate with high-risk third parties (or your whole portfolio) with in-depth IT security questionnaires.
- Build your own or access pre-built questionnaires built by industry experts.
- Auto-schedule issuance according to your framework.
- Auto-score responses and dig into detail.
Manage and Monitor
Manage projects, track completion rates and communicate with team members and respondents.
- Manage complex and simple projects efficiently.
- Track completion rates and live projects in real-time.
- Communicate with your team or cross-department, as well as with respondents.
Assess abd Remediate
Access third parties and benchmark against peers; identify risks and escalate them with third parties.
- Access all third parties in a single platform.
- Compare the performance of vendors.
- Escalate with high-risk providers
Vendor due diligence and selection
Standard and custom questionnaires
Access industry-standard IT security questionnaires, recycle questions and streamline your framework.
- Access Thomas Murray’s questionnaires library or build a custom assessment.
- Respondents can reuse answers and issuers can review responses by exception.
- Assign criticality, create question tags, and store documents for maximum efficiency.
Track, Report and Benchmark
Track and report the assessment process, create dynamic benchmarks and investigate findings with interactive analytics.
- Track respondent progress, create timelines and prompts.
- Address concerns early and add comments.
- Monitor remediation.
- Benchmark against peers.
- Use report wizard to export data and produce meaningful analysis.

Have any questions?
Have any questions?
Insights

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.

How Private Equity Hackers Choose Their Targets
Private equity firms sit at the intersection of high-value financial transactions, sensitive deal data, and an expanding portfolio of technology heavy portfolio companies – and it’s this combination that makes PE an attractive target for cyberthreat actors.