US demands incident response plans from financial organisations
The US Securities and Exchange Commission (SEC) has updated Regulation S-P to enhance the protection of customer information at financial institutions, including broker-dealers and investment advisers. These amendments mandate the creation of incident response programmes to detect, respond to, and recover from unauthorised access to customer data. Institutions must notify affected individuals within 30 days, detailing the breach and protective measures. Larger entities have 18 months to comply, while smaller entities have 24 months. This modernisation addresses technological advances and evolving data breach risks to better protect consumer privacy.

The SEC's recent amendments to Regulation S-P underscore the importance of incident response plans. By mandating that financial institutions develop and maintain these plans, the SEC highlights their critical role in protecting customer data and ensuring swift, effective responses to data breaches. The requirement for prompt notification to affected individuals further demonstrates the SEC's commitment to transparency and consumer protection in the face of cybersecurity threats.
Incident response plans are key to minimising the impact of data breaches. They provide a structured approach for detecting, addressing, and recovering from security incidents, and ensure quick and efficient responses. This reduces potential damage, protects customer trust, and ensures compliance with regulatory requirements. Effective plans include clear communication strategies, defined roles and responsibilities, and continuous monitoring and improvement, enabling organisations to handle breaches effectively and mitigate risks associated with unauthorised access to sensitive information.
Through our deep experience of helping organisation to prepare for, and respond to, a vast array of incidents, Thomas Murray’s expert team can assist with the development, implementation and testing of incident response plans tailored to the requirements of the SEC.
We combine our practical knowledge with industry best practice and the requirements of your specific business to produce an incident response plan that integrates effectively with your people, technology, and culture. Our experts can then turn our experience responding to incidents and threats into creating a tailored scenario that will stress test that incident response plan. It will realistically reflect your business’s operating environment and its risk profile.
Google Cloud glitch exposes supply chain vulnerabilities
UniSuper, a major Australian superannuation fund, recently experienced issues with account access due to a problem involving Google Cloud services. Despite having data duplicated across two Google Cloud regions, both copies were lost due to the error, impacting over 620,000 members. Such disruptions highlight the significant dependence on cloud service providers for critical business functions.
This incident underscores the inherent risks associated with supply chain dependencies in cloud services. Firstly, reliance on third-party cloud services means that any issue with the provider can directly impact the operations of dependent businesses. In UniSuper's case, an issue with Google Cloud led to service outages, affecting customer access and potentially damaging trust and reputation. Secondly, third-party cloud providers hold vast amounts of sensitive data. Any security breach or vulnerability in their infrastructure can compromise the data of all client organisations, leading to significant financial and reputational damage.
Moreover, companies must ensure that their cloud providers comply with relevant regulations and standards. The lack of direct control over third-party systems can complicate compliance efforts and increase the risk of non-compliance. Effective incident response plans must include strategies for dealing with third-party service disruptions. This incident highlights the need for robust contingency planning to ensure business continuity and rapid recovery from supply chain failures. Additionally, dependence on a single cloud provider can create a vendor lock-in situation, limiting flexibility and bargaining power. Diversifying providers and ensuring interoperability can mitigate this risk.
Organisations should conduct thorough due diligence when selecting cloud providers, assessing their reliability, security measures, and compliance with industry standards. Regular audits and reviews of third-party services can help identify potential risks early. Developing comprehensive incident response plans that include third-party risk management (TPRM) strategies is crucial for maintaining resilience and protecting sensitive customer data. By addressing these supply chain risks, organisations can better safeguard against disruptions and ensure continuity of services, thereby maintaining customer trust and upholding their reputation.
The active management of supply chains is an expectation for all businesses – as well as a critical requirement in the face of both increasing regulatory pressure and the need to reduce the risk of severe business disruption. At Thomas Murray, we have extensive experience of working with clients to understand and manage supply chain risk, and we frequently identify and assist with the management of key concentration risk.
Thomas Murray cyber trends
Malware targeting the financial sector (Global)
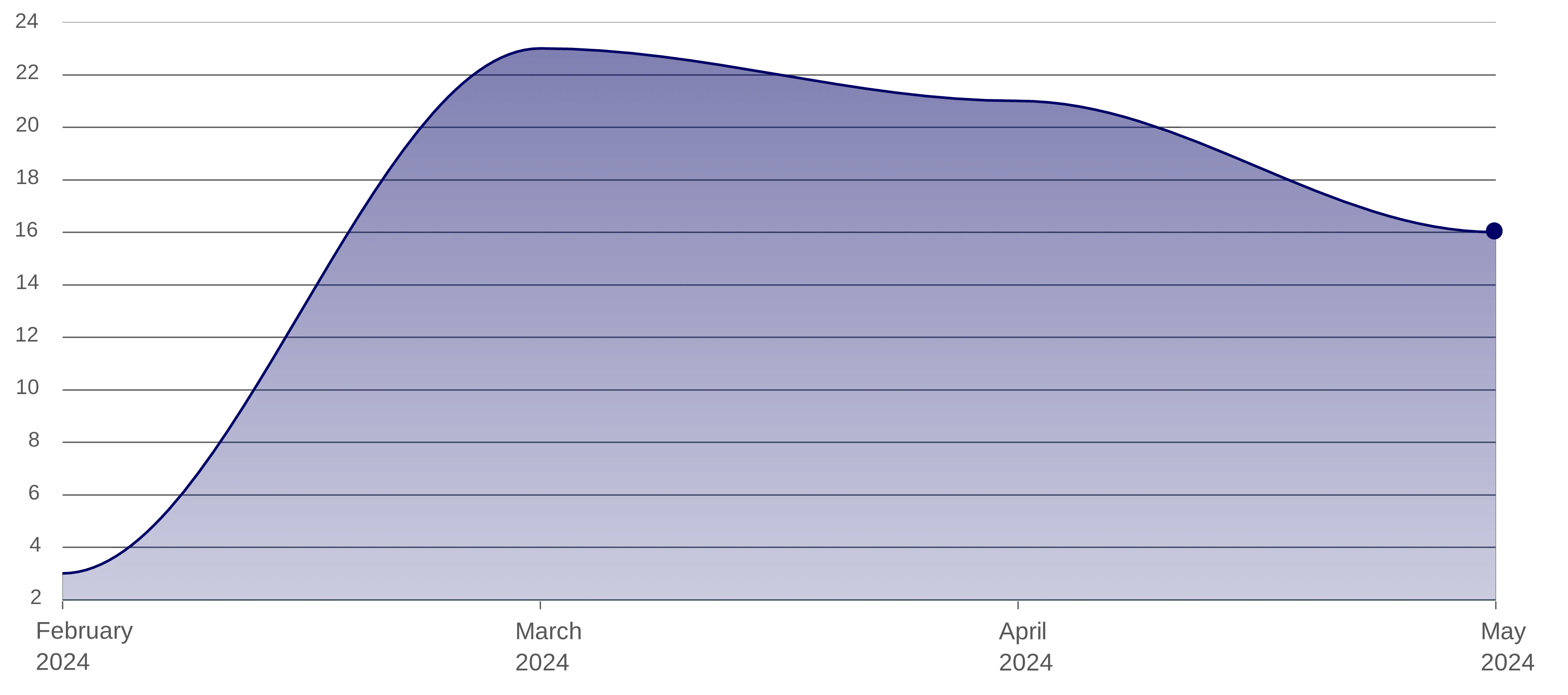
Ransomware vs Finance (last three months) – Shows no let-up in targeting
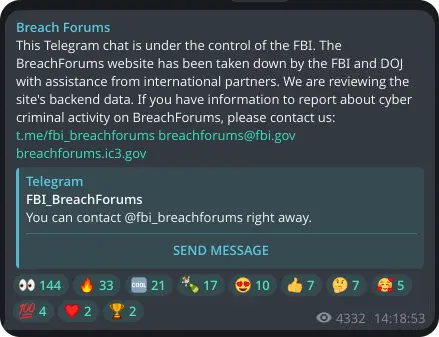
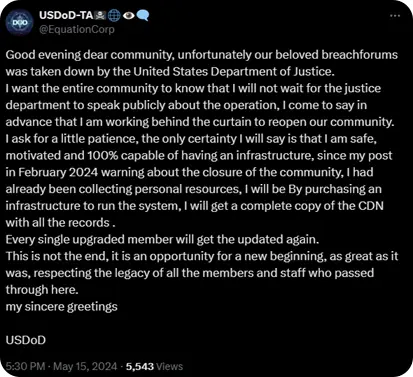
BreachForums taken down
The notorious dark web marketplace BreachForums was seized by law enforcement on 15 May 2024, though one of its administrators, the threat actor known as USDoD, has vowed that the marketplace will return. USDoD (not to be confused with the US Department of Defense) has a track record of operating dark web marketplaces and a history of involvement in many significant data breaches.
The recent seizures of BreachForums and the LockBit ransomware group's infrastructure by law enforcement are major successes in the ongoing effort to dismantle major cybercriminal networks. However, the rapid reemergence of these platforms demonstrates the resilience and adaptability of such threats.
The return/likely return of BreachForums and LockBit suggests a persistent and evolving threat landscape, where takedowns may temporarily disrupt operations but do not eliminate the underlying networks. Cybercriminals are quick to adapt, often reconstituting their communities and tools to continue their activities. This underscores the importance of continuous vigilance, advanced threat intelligence, and adaptive cybersecurity strategies to mitigate the impact of these persistent threats.
 |  |  |

Cyber Risk
We bring the best of our collective experience, energy and creative power to fiercely safeguard our clients and fortify their communities.
Insights

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
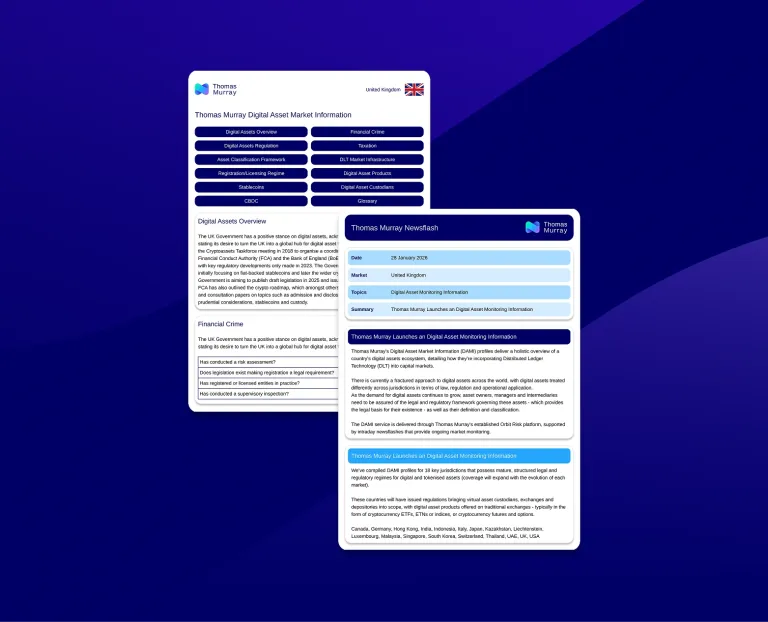
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.

How Private Equity Hackers Choose Their Targets
Private equity firms sit at the intersection of high-value financial transactions, sensitive deal data, and an expanding portfolio of technology heavy portfolio companies – and it’s this combination that makes PE an attractive target for cyberthreat actors.

