The current hype surrounding generative AI (GenAI) tools is understandable. However, there's another, potentially even more seismic technological shift taking shape: the rise of quantum computing.
Quantum computers harness the principles of quantum mechanics to perform calculations that are impossible for traditional computers. This computational power could render obsolete the encryption standards that protect our digital world and provide the basis of secure transactions, and ultimately trust, within our society.

As we advance into 2024, quantum computing is seeing a huge acceleration. IBM has unveiled a new 433-qubit processor, enhancing computational capabilities significantly beyond previous models (MIT). In parallel, atom-based quantum computers have achieved a breakthrough with 1,000 qubits, setting new standards for computational efficiency (Phys.org). These advancements, coupled with improved error-correction techniques and global collaborations, are poised to integrate quantum computing into practical applications, making 2024 a pivotal year for the technology (Techopedia).
Slow or ineffective adoption of quantum computing technologies could place an organisation at a significant competitive disadvantage; however the scale and nature of change requires careful consideration and management.
In addition to the very real advantages that quantum computing could realise for many businesses, there are also some harsh realities that need to be addressed:
- Many existing leading encryption standards are – or will be – vulnerable to decryption.
- Advanced quantum algorithms could target the complex control systems of power grids, water treatment plants, or transportation networks, causing widespread blackouts or even physical damage.
- Companies holding sensitive intellectual property, particularly in the energy, defence, or pharmaceutical sectors, could be vulnerable to quantum-enabled theft.
- Quantum computing could be used to manipulate financial markets, undermine trust in digital currencies, or attack the algorithms currently securing blockchain technology.
- ‘Harvest now, decrypt later’: The move to exfiltration of data in the current cyber security climate could be a strategy to store encrypted data for later decryption once quantum computing power becomes more accessible.
Governments and official bodies are moving as quickly as they can to stay abreast of developments, for example:
- The EU Declaration on Quantum Technologies recognises the strategic importance of quantum technologies for the scientific and industrial competitiveness of the EU.
- The US National Quantum Initiative provides a federal programme to accelerate quantum research and development for national security purposes. Significant progress has been made with recommendations from CISA and NIST to encourage organisations to create a catalogue of encryption standards employed to be ready for migration to quantum secure technologies, particularly those organisations identified as being part of nationally-critical functions.
Non-compliance with developing regulations could significantly harm a company's reputation, and eventually result in punitive measures like those set out in the GDPR/the EU AI Act. Businesses might be required to develop quantum-specific business continuity plans and regularly assess vulnerabilities throughout their supply chains.
Thomas Murray: Your partner in quantum risk mitigation
Thomas Murray, with its deep expertise in capital markets, risk assessment, and regulatory compliance, is uniquely positioned to guide businesses as they navigate the quantum revolution. Here's how we can help:
- Quantum risk assessment: Thoroughly analyse your company's infrastructure, data security, and processes to identify potential risk areas and mitigation strategies in the era of quantum computing.
- Regulatory compliance guidance: Stay ahead of the curve on emerging quantum regulations across jurisdictions to maintain full compliance. As the full potential of quantum computing is understood by national and supranational regulators, additional laws and regulations are expected. For multinational organisations operating in multiple jurisdictions, conflicting regulatory regimes will have to be understood and managed appropriately.
- Strategic consulting: Develop customised roadmaps for quantum-resistant technology integration and long-term cyber security preparedness. We ensure organisations can securely adopt quantum computing technology.
- Educational programs: Access tailored training and resources to upskill your staff in understanding the potential benefits and risks of quantum computing. Our programmes seek to inform and empower teams to make decisions in how organisations can safely optimise the adoption of quantum computing.
Conclusion
The development of quantum computing is at a watershed moment. Ignoring its potential impact puts organisations across all sectors at risk. Thomas Murray’s expertise will help you navigate this complex and rapidly changing landscape. By actively preparing now, you will gain a strategic advantage in this new, quantum era.

Cyber Risk
We bring the best of our collective experience, energy and creative power to fiercely safeguard our clients and fortify their communities.
Insights

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
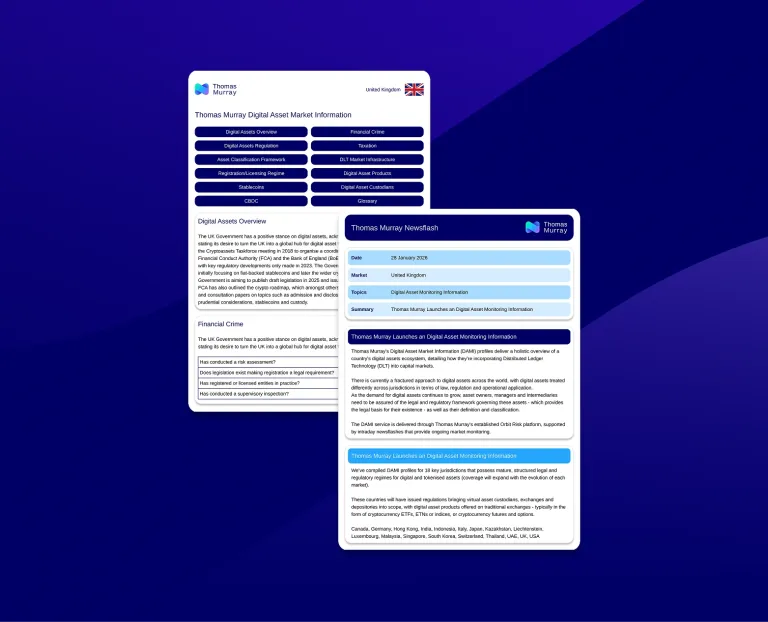
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.

How Private Equity Hackers Choose Their Targets
Private equity firms sit at the intersection of high-value financial transactions, sensitive deal data, and an expanding portfolio of technology heavy portfolio companies – and it’s this combination that makes PE an attractive target for cyberthreat actors.

