For most, the word ‘hacker’ elicits images of a shadowy figure in front of multiple screens with Matrix-like text spewing out and wreaking havoc in the world. But I am the other kind of hacker, one who works within ethical boundaries to help organisations improve defences – a ‘penetration tester’, or ‘pen tester’ for short. (I prefer this term as, unlike ‘hacker’, it has positive connotations, and I don’t get a look of disgust or fear that I might be malicious and evil!)
Pen testers are usually passionate, inquisitive, have a knack for breaking things to understand how they work and to stop attackers from exploiting vulnerabilities. But what exactly does a day in the life of a pen tester look like?
Morning
The day begins with a cup of coffee, as I review my schedule and objectives for the day. Depending on the assignment, we can be testing either external perimeters, internal networks or attacking web applications for our clients. This week we are helping a financial services organisation to evaluate and find vulnerabilities in its internal network.
Internal network penetration tests involve being inside an organisation’s network, and having access to all the elements that a normal user would. This type of engagement skips the external perimeter, which is usually protected by firewalls, and allows an organisation to check the security of its internal systems, which can help them to understand what an attacker may target after they gain access.
Firewalls are an obstacle to attackers, but this does not mean they are the best protection. Some organisations expose applications, so they can be used by external parties.
Anecdote: During a previous engagement, I managed to gain access to (OK, hack) a web application that gave me access to the internal network of an organisation in less than three hours.
At Thomas Murray, we collaborate with our cyber threat intelligence (CTI) analysts to gather intelligence on potential threats and recent attack patterns. Our internal briefings cover everything from the geopolitical tensions influencing cyber crime, to technical details about known vulnerabilities and exploits. This helps us understand the landscape and contextualise our meetings, client calls, and findings for each organisation.
Communication is key, so we let the client know we will begin testing and objectives for the day, using our selected communication channel. In addition, any changes, updates, checks or interesting findings are posted in the channel. Today will be focused on scanning and identifying vulnerabilities as we progress.
Mid-morning
We begin the scanning stage, where we find out as much as possible about the environment we’re testing. Think of it as checking the reviews and menu of a restaurant before you visit it.
Information provided by the client and scanning tools (such as Nmap and Nessus) help us to identify web applications, servers, and any open ports that might be weak links in the network that allow access to the organisation’s crown jewels. This scanning phase is crucial – a thorough understanding of the system minimises the risk of issues or downtime during the test.
Informative
- Nmap – A tool that helps scan networks, it outputs the open services, version information and operating details that may come in use.
- Nessus – A tool that helps scan networks, but also helps us identify the possible existence of a vulnerability within the environment.
While the scans are outputting data, I work to analyse the information and plan my next moves. I identify that the organisation has several devices that are running out-of-date operating systems, several multi-function printers and lots of web applications.
Afternoon
Focused after a simple lunch of coffee and a healthy dose of determination, I unleash my arsenal of hacking tools. But before we begin testing, I inform the client that we may have some interesting findings and we are going to probe further. This allows them to prepare for any alerts that could be triggered from the security systems. (Our main aim is to identify vulnerabilities, disregarding stealth during this test.)
We begin with testing the login forms for weak/default credentials, probe for SQL injection vulnerabilities (a way to steal data) and try to exploit any misconfigured systems. Boom! We have access to a Kyocera MFP printer with the default credentials – now to rummage around in the settings to see if there is any interesting loot.
We find credentials that allow the printer to send scans as email or save them to shared folder. This is interesting as, so far, we did not have any credentials to log into the systems with. We like to start as ‘unauthenticated’ and work our way from there to the crown jewels.
So, we extract the credentials by changing them and pretending to be the authentication server, which the printer accepts. It sends us the password in plain text. This part of the engagement is exhilarating, and you get a rush of adrenaline that focuses the mind even further. We can now use these credentials to locate even more loot on the network.
As we now know where the scans are being saved, and we have the user credentials that saves them, it now seems likely that we have access to some interesting data that contains ‘personally identifiable information’ (PII). We let the client know our finding. The client acknowledges our discoveries so far and asks us to see how much further into its network we can get.
Side quest: A colleague carrying out a phishing social engineering engagement needs an extra pair of hands to collate a list of users that we will be targeting for a ‘red team’ engagement.
I extract a list of names and emails using open-source intelligence (OSINT) – professional networking sites are great for this information, as we can also gather an individual’s job title and probable location. Excitedly, with some Microsoft Excel magic, I prepare the list of the ‘targets’ and send them over, while my colleague finishes crafting the malware that will be sent to them.
Evening
Using the credentials, we look to the authentication server and see if we can find any misconfigurations that may allow us to elevate our privileges further (we want to evaluate how far we can get, can we access customer data?).
As I used to be a system administrator, I know how these systems work; sometimes administrators have scripts that contain hard-coded passwords. On this occasion, my gut instinct is correct and, after trawling through hundreds of files, we find a script that was intended to send backup reports via email. I attempt to validate the found credentials and, as my inkling led me to believe, the user is an active administrator (aka Domain Admin), which means we can access most systems in the network. After letting the client know, we prepare ourselves for tomorrow, and identifying the next vulnerability.
Conclusion
As the day winds down and I shut down my computer, a sense of satisfaction washes over me. The life of a penetration tester requires constant vigilance, creativity, and collaboration. Sure, the days can be long, and the challenges never-ending, but the thrill of the hunt and the knowledge that I’m making a real difference feels great.
By working closely with CTI analysts and incident responders, penetration testers ensure that defences are not just theoretical, but tested and proven against real-world tactics and techniques. After all, who wouldn't want to be a hacker who helps?

Cyber Risk
We bring the best of our collective experience, energy and creative power to fiercely safeguard our clients and fortify their communities.
Insights

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
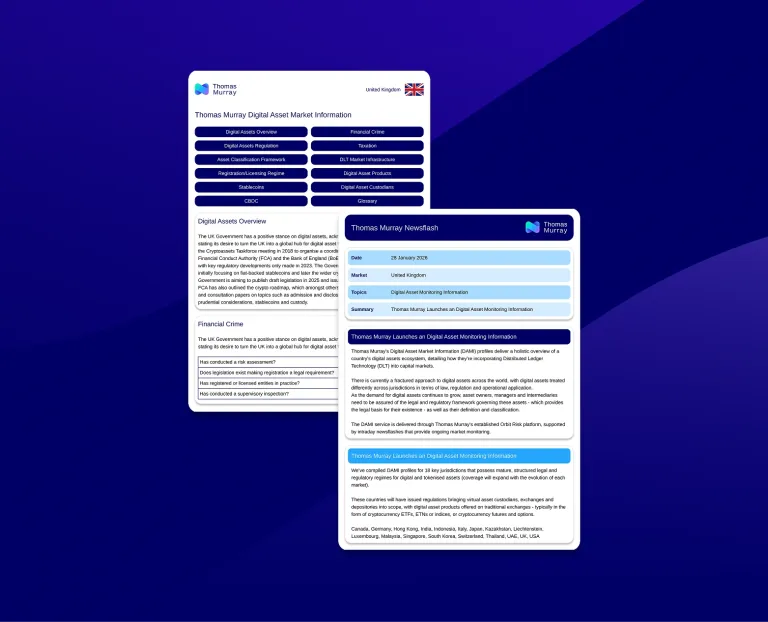
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.

How Private Equity Hackers Choose Their Targets
Private equity firms sit at the intersection of high-value financial transactions, sensitive deal data, and an expanding portfolio of technology heavy portfolio companies – and it’s this combination that makes PE an attractive target for cyberthreat actors.

