Valentina Martinez initially joined Thomas Murray as a data analyst. But she is now with our Cyber Risk team, where her existing skills complement the team's capabilities.
In this week’s Cyber Series, Valentina explains the parallels between her previous role and her current one, the contribution a data analyst makes to a cyber security team, and how an analyst's ability to clearly present the findings of complex data benefits organisations as they build their cyber security defences.

There is some truth to the assumption that cyber security teams are full of experts in information technology, software engineers, and specialists in hacking techniques – though that is only part of the picture. Many people with different skills, experiences, and backgrounds also contribute to a cyber security team’s core operations and effectiveness.
This is certainly true for me, as although I’m now a cyber risk analyst my previous experience was mainly as a data analyst in sectors such as social consulting and start-ups.
Fortunately, there is more in common between data analysis and cyber risk analysis than I initially thought. My skills are proving to be helpful in various areas of the team, specifically in cyber threat intelligence (CTI) where the skills of a data analyst are highly applicable.
I even made a table to highlight how the shared principles of both fields focus on data-driven decision-making:
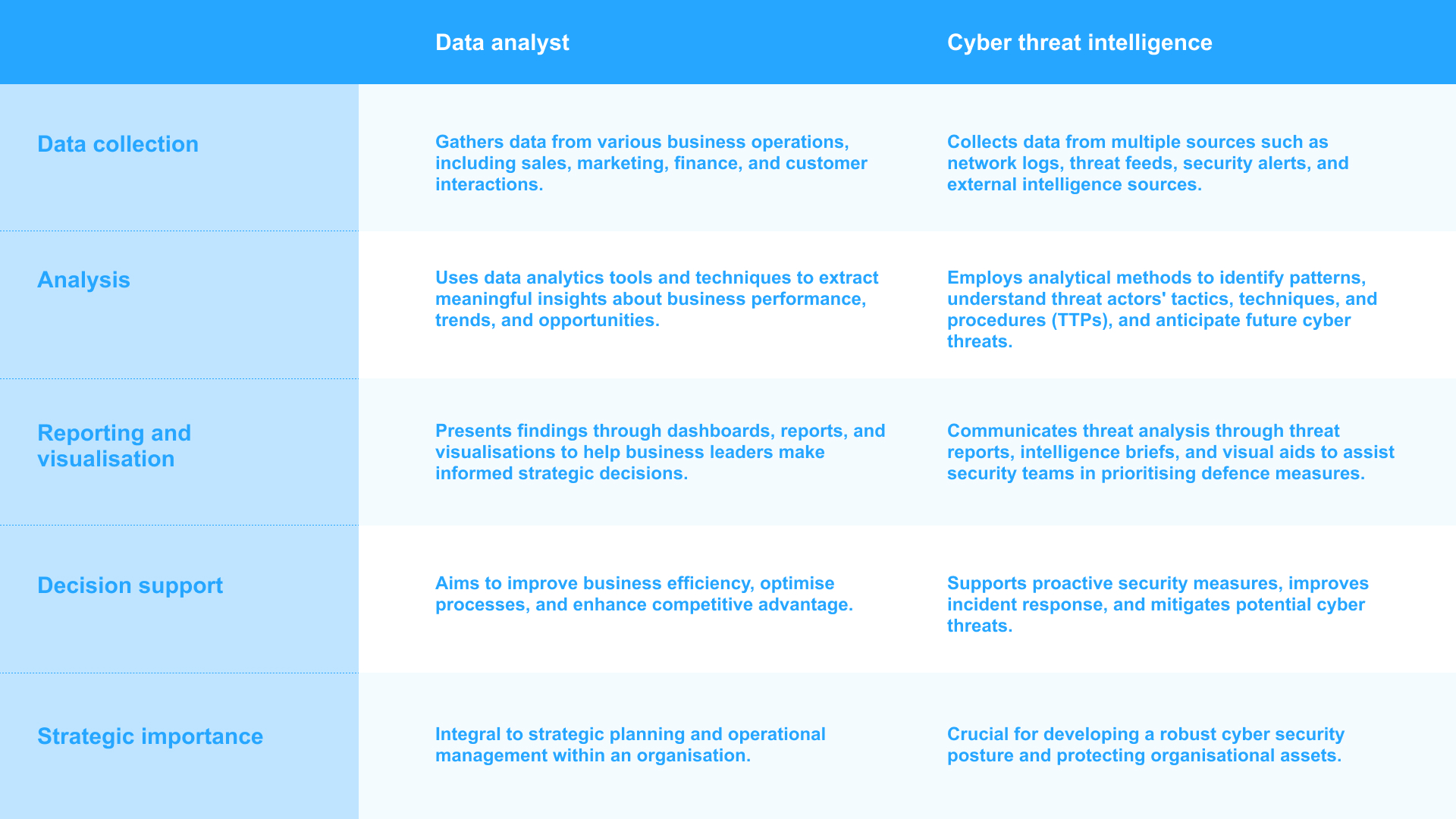
The ability to generate actionable insights after interpreting complex data sets to identify potential threats and vulnerabilities will help organisations to anticipate, detect, and mitigate cyber threats efficiently. That’s where I come in.
It is hard to say what my ‘typical’ day looks like as the role is so varied. For example, it could start with creating cyber threat summary reports on various countries. This involves:
- analysing threat types;
- identifying the most targeted sectors; and
- leveraging my background to make these analyses comprehensible for both non-technical audiences and experts.
I also design visually clear and relevant charts to meet the report’s objectives.
Then I might be involved in cyber risk assessments, and in the creation of a risk quantification model that allows us to determine the financial risk of the most common cyber threats. This is of particular interest to me, as it was a paper I contributed to on cyber threat and the global economy that first got me thinking about a new career path.
Given how busy threat actors are, it’s likely that at some point I will assist in gathering data relevant to analysing their tactics. This data will later help in conducting an analysis of the most common tactics, allowing for better management of efforts to prevent or remediate attacks.
Over the course of the entire day, I continuously monitor threats and developments in the cyber world so that I can feed that information into our reports.
The most relevant skills here are analytical and communication ones, combined with strong problem-solving abilities as you need to be able to collect, analyse, and manage data to ensure accurate and actionable insights. Clear and concise reports on security incidents, vulnerabilities, and threat intelligence, complemented by effective charts and graphs, aids in communicating these findings to a wide range of audiences.
A data analyst needs to get to grips with cyber security principles — including various types of cyber threats, attack vectors, and defence mechanisms — to make meaningful contributions to a cyber security team.
By refining these analytics skills, data analysts can provide valuable insights into the nature and scope of cyber threats, which are essential for developing cyber security strategies. This ongoing learning journey is both challenging and rewarding, and I would encourage other data analysts who are interested in cyber security to look into a career path that can take you to unexpected and interesting places.

Cyber Risk
We bring the best of our collective experience, energy and creative power to fiercely safeguard our clients and fortify their communities.

Thomas Murray cyber alerts
Subscribe to stay up to date with developing threats in the cyber landscape
Insights

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.

How Private Equity Hackers Choose Their Targets
Private equity firms sit at the intersection of high-value financial transactions, sensitive deal data, and an expanding portfolio of technology heavy portfolio companies – and it’s this combination that makes PE an attractive target for cyberthreat actors.


