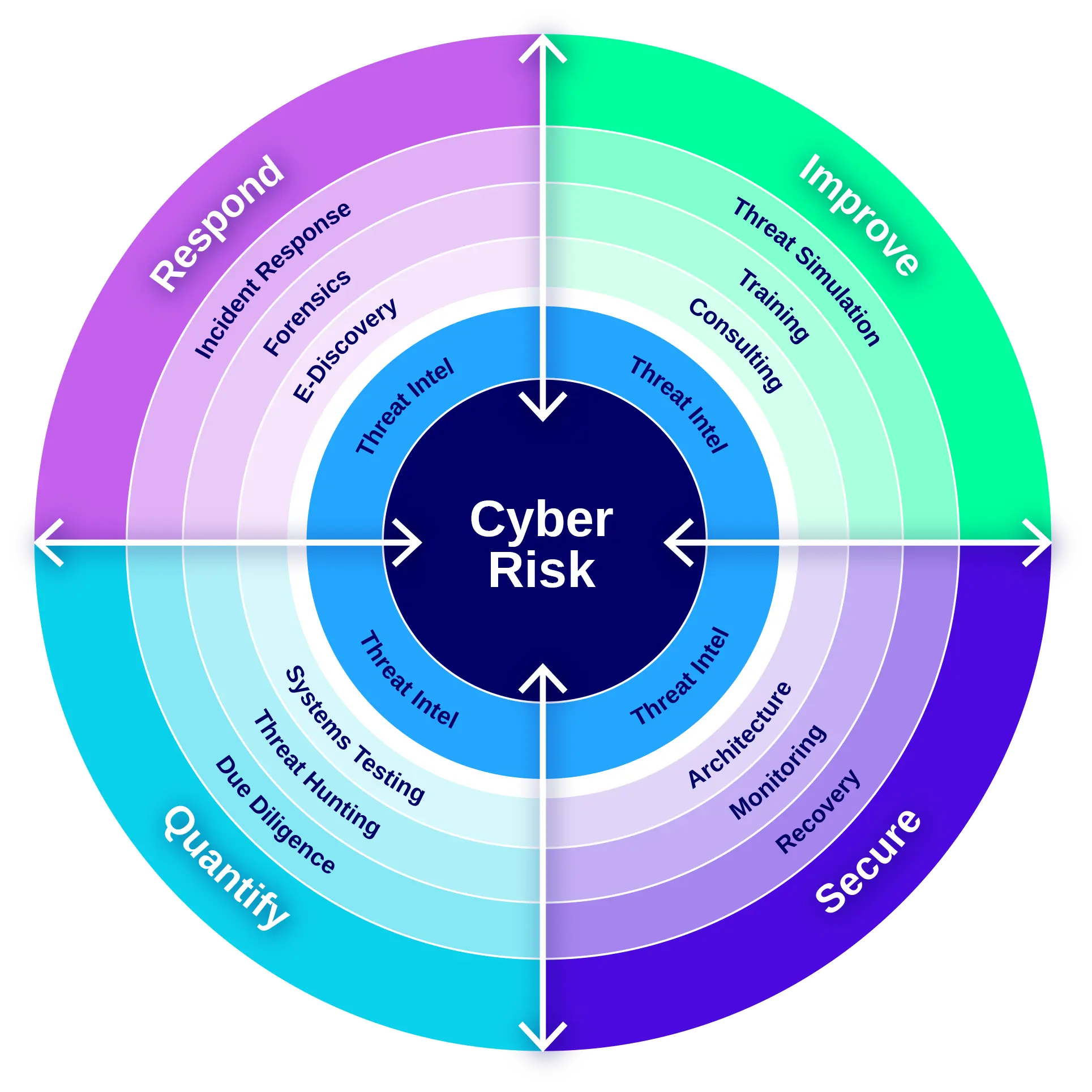
Respond
Introducing our formidable suite Respond – an array of services meticulously crafted to channel our collective prowess in navigating technical challenges, legal intricacies, and complex data requirements. We stand as the premier resource for swift, decisive solutions.
This isn't your ordinary response team
Incident readiness
Proactive preparation for potential challenges.
Incident response
A decisive force in confronting and overcoming disruptions.
Active threat hunting
Proactively pursuing and neutralising threats with precision.

Forensic services
Uncovering digital traces often overlooked by others.

Expert services
Our seasoned specialists serve as your advantage in seeking the truth.

eDiscovery services
Supporting litigation by making the navigation of complex data and digital evidence seamless.

Thomas Murray cyber alerts
Subscribe to stay up to date with developing threats in the cyber landscape
Improve
Our Improve services are strategically engineered to rigorously test your digital capabilities within a controlled framework.
Join us in strengthening your digital defences and preserving value.

Operated by battle-hardened industry experts, the diverse spectrum of Improve services encompasses:

Training
- Executive briefings
- Tabletop exercises
- First responder training
- Cyber awareness workshops
Cyber risk consulting
- Cyber strategy formulation
- Governance enhancement
- Audit
- Compliance evaluation
- Risk management
- Comprehensive assessments
- Controls optimisation
Third-party risk management
- Enhance the framework for cyber risk management across the supply chain

Secure
Our security services are a blend of cutting-edge technical prowess and strategic insight, designed to proactively fortify your defences.
Our seasoned team has orchestrated operational excellence for blue chip organisations worldwide, delivering unparalleled insights and expert counsel to safeguard our clients' enterprises. Elevate your organisation's security to meet escalating cyber threats.
Fuelled by the relentless determination of our team, our services include:

Proactive security monitoring – vigilant safeguarding against potential threats with a proactive and pre-emptive approach.

Portfolio security monitoring – defending the value of your investment and reputation through informed risk management.

Security architecture services – crafting bespoke controls and security frameworks to fortify the structural integrity of your corporate landscape.

Recovery and remediation services – helping you execute swift and precise responses to recover and remediate security breaches.

Business continuity advisory and assessments – strategically navigating potential disruptions, providing advisory services, and conducting thorough assessments for seamless business continuity.
Quantify
Achieve the pinnacle of corporate resilience in the ever-evolving landscape of cyber security. Our suite of services is designed to pinpoint areas ripe for enhancement. Elevate your organisation's risk management strategy and empower it with actionable insights for strategic change.
Define a new standard in security excellence – discover how Quantify can fortify your corporate cyber security.

Our suite of services, curated by our team of seasoned industry experts, includes:
Cyber due diligence

Better inform your financial transactions by uncovering the risks embedded in digital infrastructures with our methodical approach.

Proactive threat hunting

Safeguard your corporate ecosystem by pre-emptively identifying and neutralising potential threats.
Systems testing

(Vulnerability assessments and penetration testing) Ensure the resilience of your systems through comprehensive testing and strategic fortification.

External attack surface monitoring

Maintain a vigilant watch over your own, and your community's, external digital footprint to pre-emptively address vulnerabilities.

Custom threat intelligence research

Use threat intelligence to decode risk and master the ever-shifting digital frontier.

Cyber investigations
Thomas Murray’s investigatory capability is founded on our deep experience of helping our our global clients analyse events around criminal and civil matters with thoroughness, legality, and effectiveness.
Why Thomas Murray?
These services are the pillars of consulting excellence within Thomas Murray's cyber advisory practice. Our unified team of experts will support you as your needs evolve and your requirements grow.
We embed threat intelligence in all that we do and the language we speak. This ensures that you understand the relevance of our work and knowledge as they relate to the context of your business. We ensure that you are uniquely positioned to manage your cyber risk proactively.
Our team is relentlessly focused on helping our clients identify and manage cyber risk: we are responsive, dependable, and of the highest integrity, ensuring that value is realised. We put your needs at the centre of everything we do.
We safeguard clients and their communities
Insights

Safeguarding Clients: Elevating Legal Services with Advanced Threat Intelligence
In an era of escalating digital threats, law firms have a unique opportunity to transform their service offerings by integrating cutting-edge cyber se

Thomas Murray Partners with Socura to offer Managed Detection and Response to clients that need support to stop cyber threats 24/7.
The collaboration will see Thomas Murray offer Socura MDR to help its clients proactively identify and respond to threats.

Thomas Murray and Crimson7 Announce Strategic Partnership to Modernise Threat Informed Security
Thomas Murray and Crimson7 are partnering to combine their expertise and create innovative solutions for tackling key cyber security challenges.

Thomas Murray and askblue partner to support financial institutions in meeting the Digital Operational Resilience Act (DORA) requirements
Thomas Murray and askblue are collaborating to provide services that help financial institutions comply with DORA requirements.
Thomas Murray is a proud member of the North West Cyber Security ClusterThe North West Cyber Security Cluster (NWCSC) is a collaboration of cyber security professionals and experts in the North West region. The NWCSC aims to promote innovation, support skills growth, and develop a robust cyber security ecosystem. |