We provide powerful solutions for the world’s leading risk specialists.
1,000+

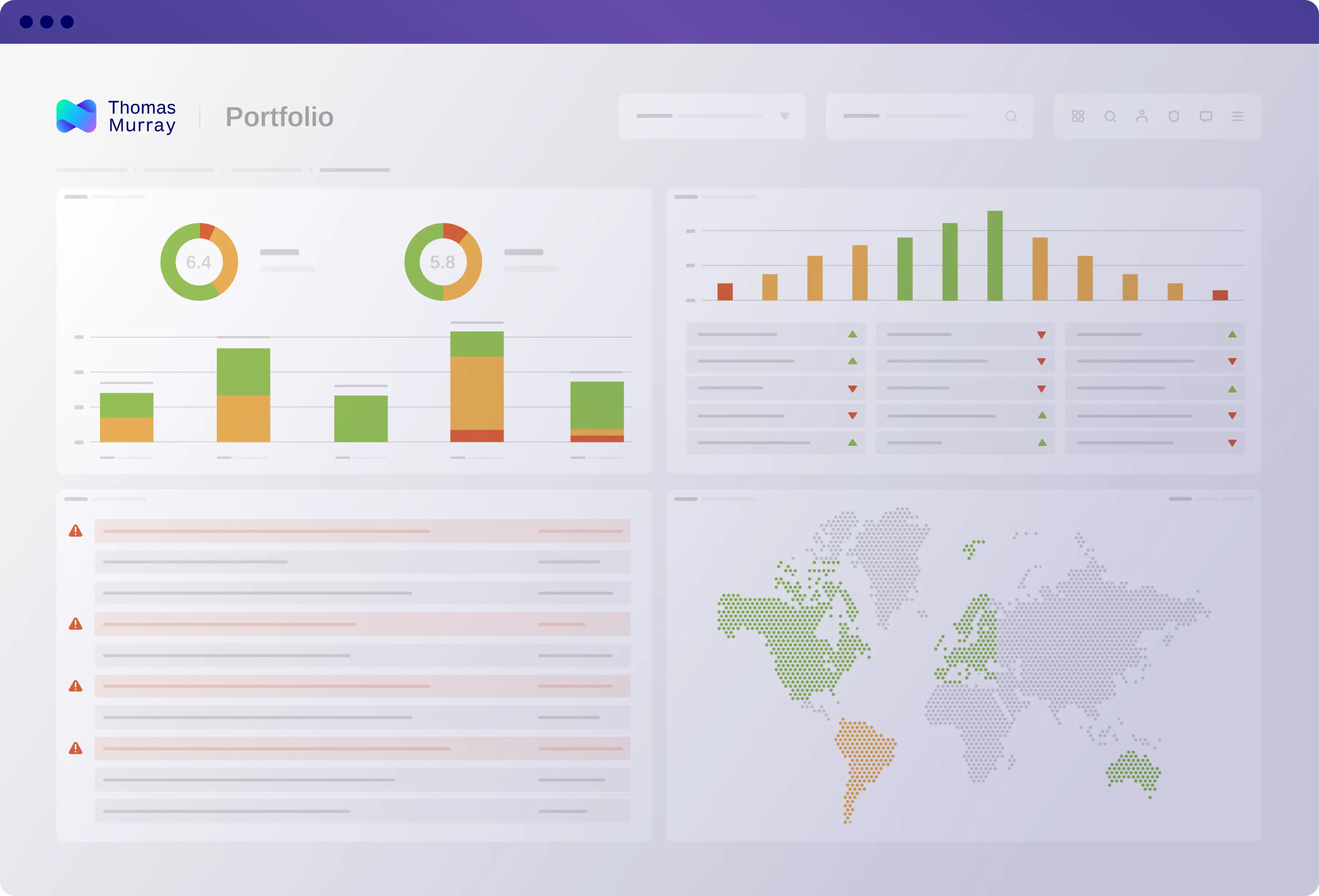
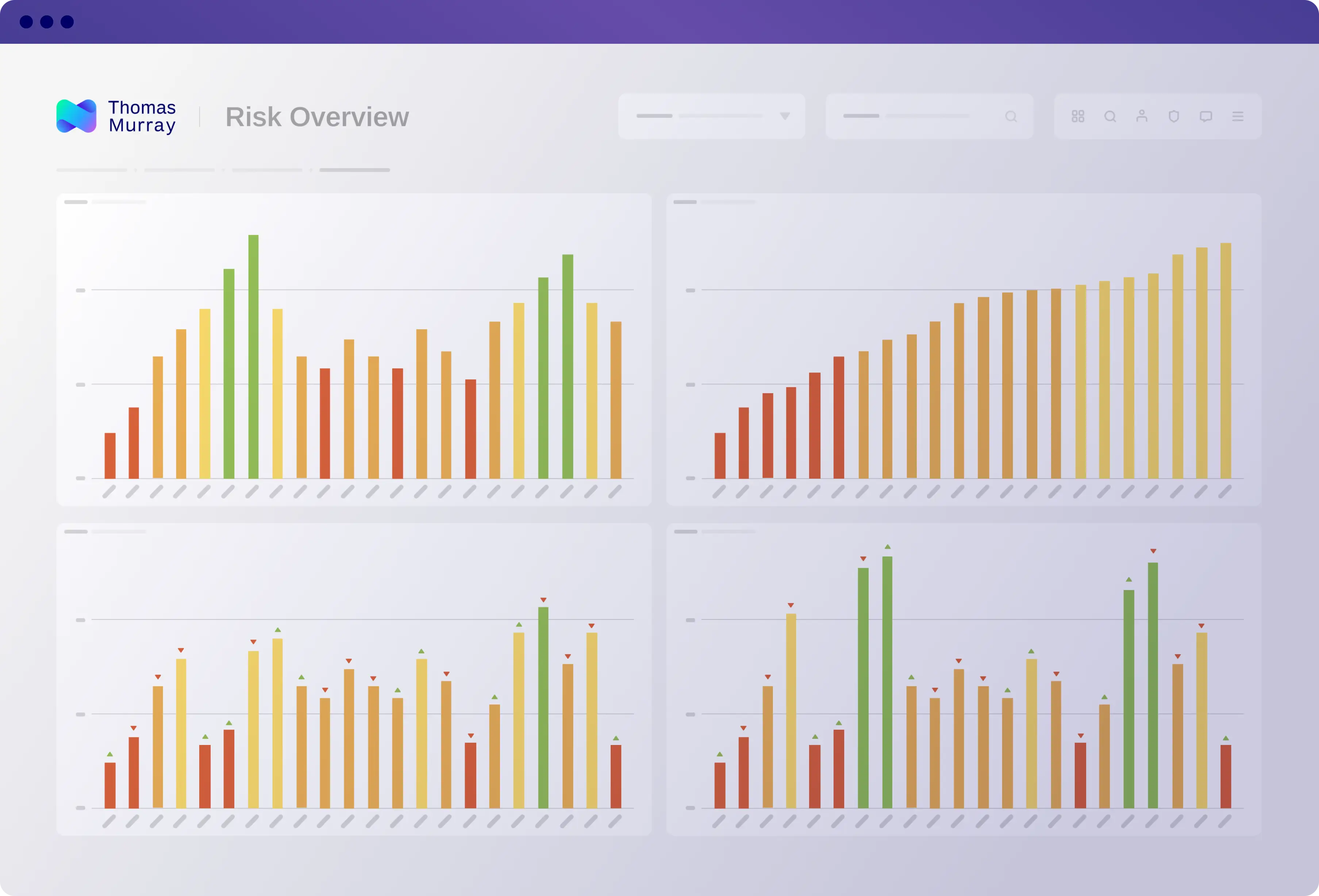
My portfolio risk dashboard
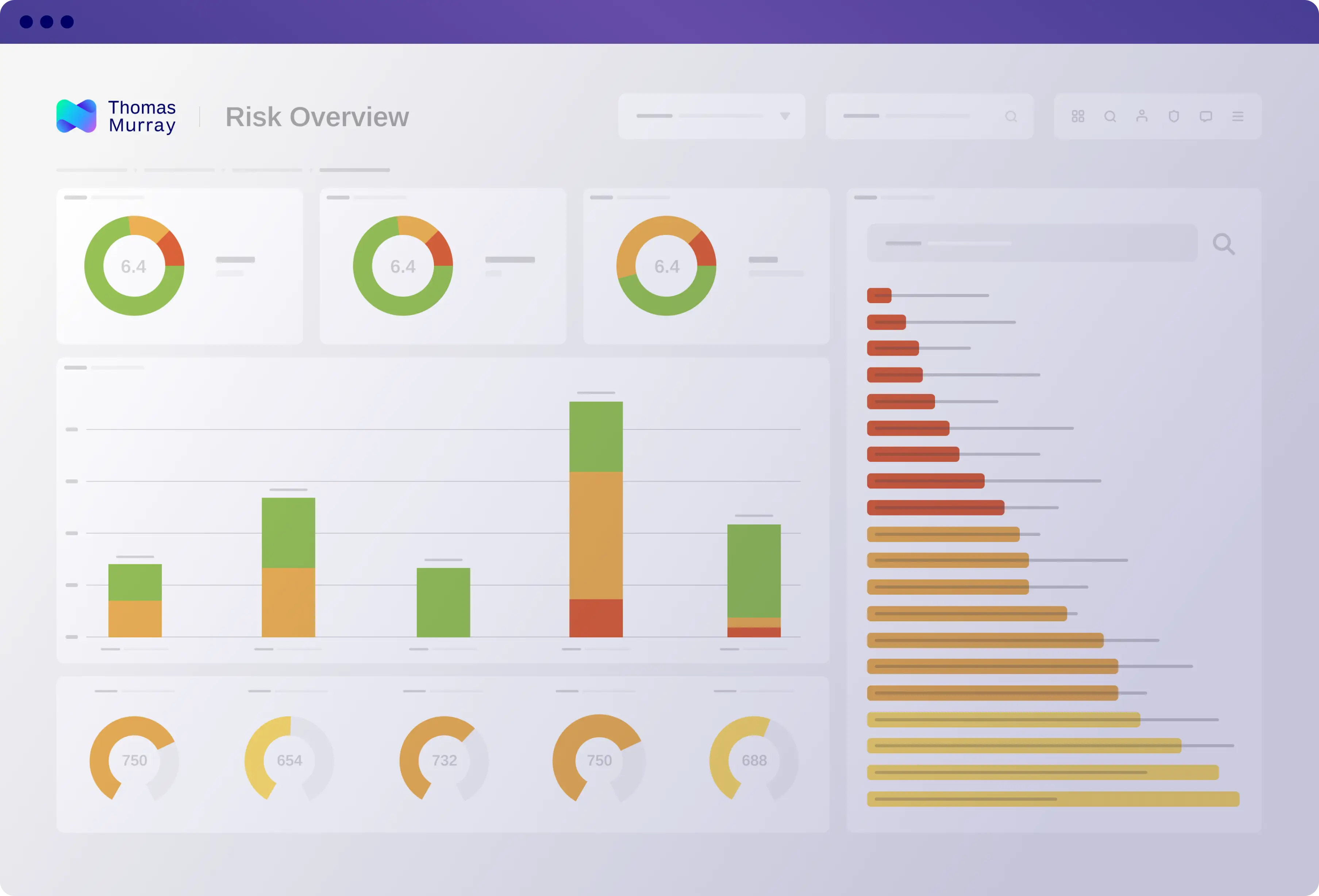
Gain a bird's eye view of your third-party network, showing you all your monitored entities on one dashboard. Identify issues, monitor trends, be informed.
- Real-time risk assessments of monitored entities
- Threat intelligence score distribution and trends
- An easy-access inventory of all third parties
- Worldwide coverage mapped across service providers
- Captured newsflashes and critical alerts
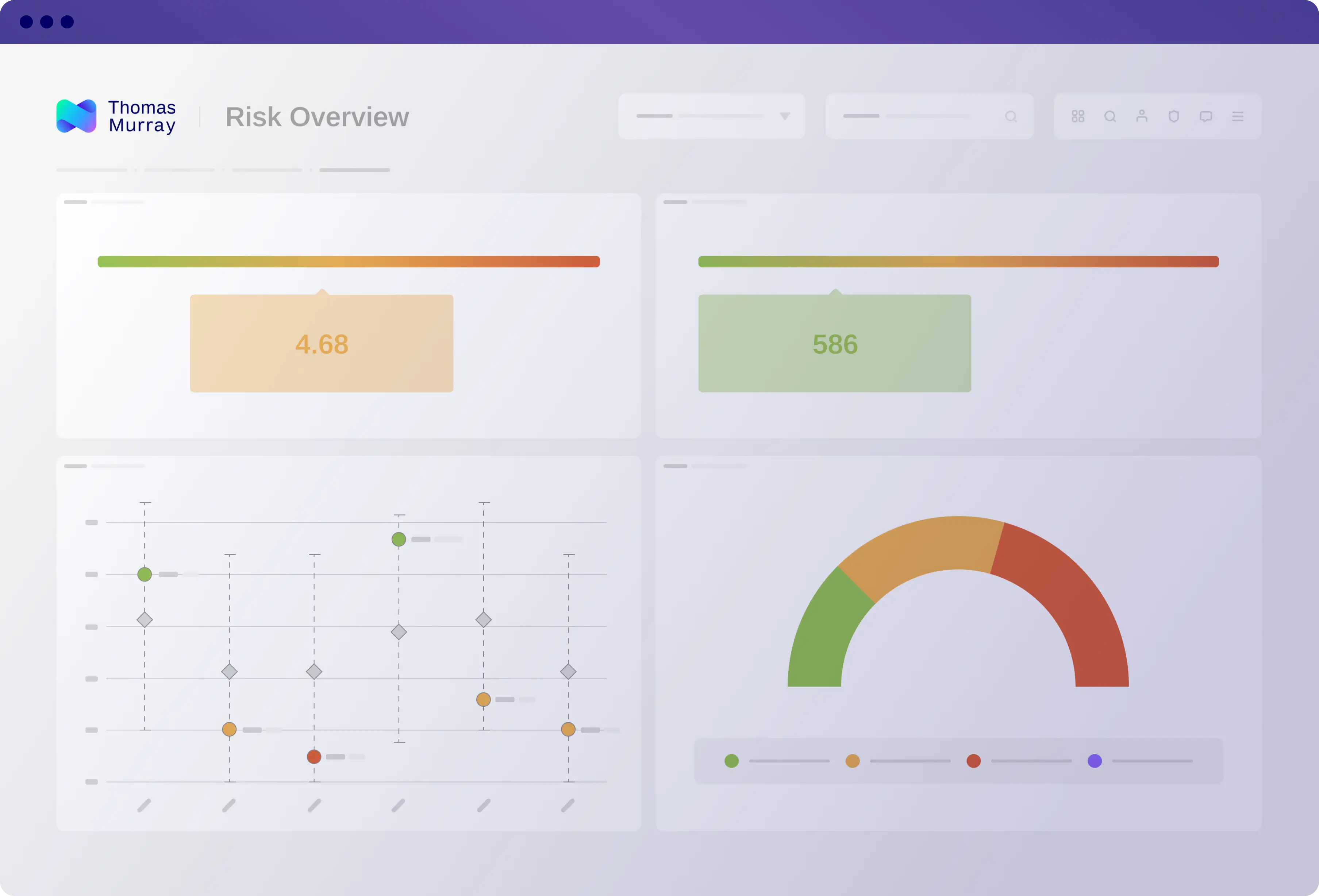
Enhanced risk view
View a comparative analysis of your service providers, with the ability to drill into the detail. Thomas Murray’s risk assessments, or your own methodology, will highlight the risks you’re exposed to.
Incorporate additional data feeds via API, and other risk factors such as security ratings or ESG data.
Structured data profiles
Thomas Murray provides standardisation and efficiency to the industries that need it. Our users provide data once, to be shared multiple times. Our platform aggregates multiple data sets from separate sources, and generates a comprehensive assessment. Data validation mechanisms and audit logs ensure transparency and accuracy.

Have any questions?
Have any questions?
We safeguard clients and their communities

Petroleum Development Oman Pension Fund
“Thomas Murray has been a very valuable partner in the selection process of our new custodian for Petroleum Development Oman Pension Fund.”

ATHEX
"Thomas Murray now plays a key role in helping us to detect and remediate issues in our security posture, and to quantify ATHEX's security performance to our directors and customers."

Northern Trust
“Thomas Murray provides Northern Trust with a range of RFP products, services and technology, delivering an efficient and cost-effective solution that frees our network managers up to focus on higher Value activities.”
Insights

5 Key Takeaways from a Deal Hacker: What PE Firms Should Look for When Doing Cyber Deal Due Diligence
Are your private equity deals safe from cybercriminals? The answer is very much ‘no’. Deals are being compromised, money is being lost, and reputations are being affected.

Why Cybersecurity Due Diligence is Critical to Deal Completion
It’s a common story: after months of meticulous financial, operational, and market analysis, a critical finding emerges in the final weeks before deal closure – threatening what seemed like a near-certain transaction with a three-month delay.

DORA Compliance Checklist: Practical Guidance for Q4 and 2026
Our structured, expert-led checklist, will help you to prioritise and demonstrate readiness to supervisors and regulators.

Ransomware at Europe’s Airports: Case for Community-Driven Third Party Risk Management
The recent ransomware attack on Collins Aerospace’s Muse software, which brought chaos to airports across Europe, serves as a stark reminder of a critical gap in how organisations approach Third Party Risk Management (TPRM).
Contact an expert