Navigating DORA’s ICT incident notification requirements
In the July edition of DORA Digest, we discussed the various regulatory technical standards (RTS) and implementing technical standards (ITS) that support the implementation of DORA’s regulations.
The ability to report incidents and threats to the regulatory supervisory bodies are core to the very intention and objectives of DORA. It is estimated that there are more than 22,000 entities within the scope of the regulation, so having specific reporting requirements is vital to ensuring information and communication technology (ICT) incidents and potential cyber security incidents can be processed at speed and at scale.


This month, we delve deeper into one of the joint technical standards on major incident reporting and the implications for organisations within scope of DORA.
The joint technical standards are a combination of the RTS designed to specify the reporting of major ICT-related incidents and the ITS designed to establish the reporting details for major ICT-related incidents: Article 20(a) and (b).
The European Banking Authority has submitted its final draft on these joint technical standards on major incident reporting to the European Commission for adoption. The draft recommendations (which are expected to remain unchanged) broadly cover the following:
- The RTS setting out the general reporting requirements around details of what information is to be included in incident reports, such as the type of incident, the affected entities, and so on.
- Initial notification requirements, including the date and time of detection and classification, a description of the incident, and the classification criteria applied.
- Intermediate incident reporting, including additional data points. These might be a detailed impact assessment, actions taken, and any updates on the incident's status.
- The final incident report focuses on root cause analysis, resolution measures, and would include an economic impact assessment.
- The ITS provides standard forms and templates for reporting incidents, ensuring consistent data collection and reporting processes.
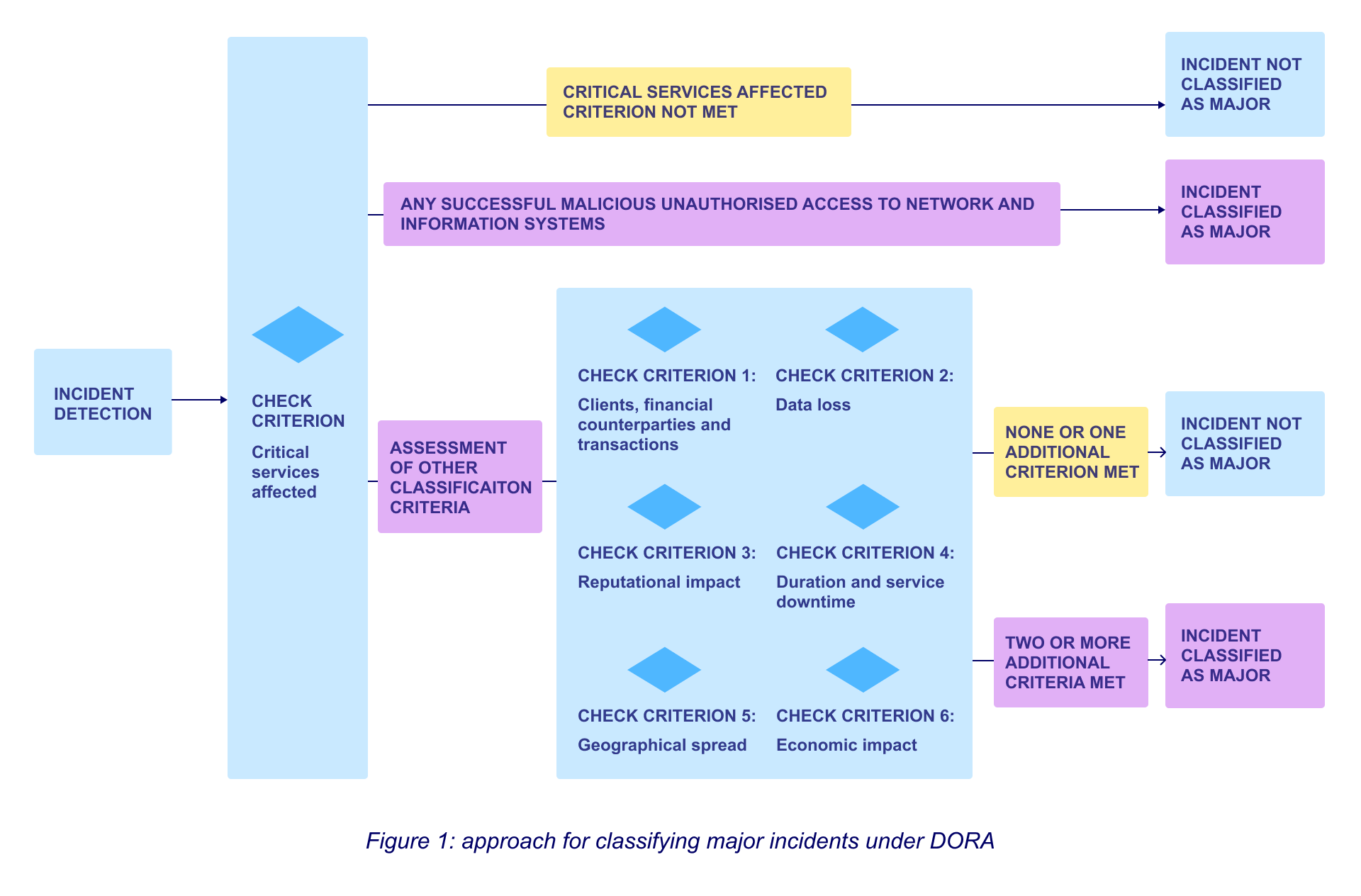
Reporting timelines depend on the ICT incident classification. Let’s have a look at classification requirements for major incidents:
Potential challenges to meeting reporting requirements
The key data and information required for these ICT incident notifications may be challenging for organisations to collate, populate, and report.
Initial notification
Although the initial data fields for this notification are limited, it will be a challenge for most organisations to comply within the specified four-hour timeframe.
As expected, it includes basic requirements such as organisational and contact details. But initial information about the incident itself is also required, including:
- when and how the incident was discovered;
- when the incident was classified as major; and
- a description of the incident, and whether it is believed to have originated from a third party or another financial organisation.
Intermediate notification
These data elements must be included in the intermediate notification, which is to be prepared within four days of an incident occurring. Again, this is a short timeframe that presents financial entities with a significant challenge.
Impact on financial counterparties
To accurately determine the number and percentage of affected financial counterparties, the organisation may need:
An accessible system that outlines the entities that could be impacted by an incident support identification or tagging of counterparties;
to form a multidisciplinary team with extensive business knowledge of processes and the broader supply chain within which the financial entity exists; and
develop methods to both record financial counterparties in the system and correlate systems data with business operations
Reputational impact assessment
Providing information on reputational impact and its context depends on two key factors:
the existence of a robust framework for assessing reputational risk; and
the presence of a dedicated function responsible for formulating reputational risk assessments and validating these assessments for regulatory reporting purposes.
Without these elements in place, it would be challenging to accurately gauge and report on reputational impacts.
Final notification
The final notification must specify the amount of gross direct and indirect costs and losses, and the cost of financial recoveries.
Gathering this information would require the incident response team to coordinate with business and/or finance teams that are not usually actively engaged in incident response activities.
It may also require the finance team to refine its processes, so it could record the losses and recovery costs as required by DORA.
Addressing the challenge
DORA outlines explicit reporting requirements that cover a wide range of information that teams from across an organisation will have to effectively collate and analyse.
A primary input into the process will be the scope of the incident and the services affected. Ultimately, this will require an extensive understanding of the organisation’s own processes, services and technologies.
Once an incident has been detected, and the services impacted understood, decisions will need to be made based on an assessment of the assessing wider criteria using the chart (Figure 1). Making these decisions accurately demands input and analysis from across the entire organisation.
Although teams may be willing to assist, it will be the speed at which their responses can be submitted and considered that will determine whether DORA’s short reporting timelines are met.
DORA is stricter in its incident reporting requirements than almost all other comparable regulations. Affected entities that assume their existing incident respondent plans will be adequate are in for a rude shock.
The hard reality is that many organisations will not have considered or formally implemented all parts of their DORA notification plan data points. And, of those organisations that have had discussions about their incident preparedness, it is likely that their preparations have not involved all the key people who need to be involved.
There is not much time left to address this challenge – but there is time, nonetheless.
Urgent actions
A programme of tabletop exercises should be planned and executed. Increasing the organisation’s collective knowledge and awareness of the reporting requirements should be a primary consideration.
Engaging teams that have previously never been part of incident response is key to meeting DORA’s extensive obligations. Evaluating the economic impact of a cyber incident, for example, will require input from individual teams that are unlikely to have experience of being consulted during a cyber incident. Coaching them through what will be expected of them from now on is essential.
Existing plans, processes, procedures and wider documentation will need to be reviewed and amended to encompass the additional regulatory requirements.
Our recommendation is therefore to start giving this aspect careful thought and planning now, if this hasn’t been done already. Like other incident response strategies and recommended strategies, the precise reporting responsibilities should be organised, recorded, and – above all – tested and verified.
Are you ready for DORA?
With a deadline of January 2025 to be fully compliant with DORA, the Thomas Murray Executive Readiness for DORA Workshops present an opportunity for executives and board members to understand the scope and implications of DORA for their organisations. This includes understanding your organisation's current exposure to regulatory enforcement and punitive actions for non-compliance.


Compliance Digest Newsletter
Subscribe to DORA Digest and stay up to date with the key issues
and developments unfolding as the countdown to DORA begins.
We safeguard clients and their communities

Petroleum Development Oman Pension Fund
“Thomas Murray has been a very valuable partner in the selection process of our new custodian for Petroleum Development Oman Pension Fund.”

ATHEX
"Thomas Murray now plays a key role in helping us to detect and remediate issues in our security posture, and to quantify ATHEX's security performance to our directors and customers."

Northern Trust
“Thomas Murray provides Northern Trust with a range of RFP products, services and technology, delivering an efficient and cost-effective solution that frees our network managers up to focus on higher Value activities.”