Background: Why DORA, and why now?
The French law firm Spitz Poulle Kannan, which specialises in financial regulation, was kind enough to answer some of our burning questions about the Digital Operational Resilience Act (DORA). When asked why the EU was regulating the use of information and communication and technology (ICT) now, they quoted from the September 2020 DORA impact assessment: “The financial sector has become as much about data and technology as it is about money and capital.”

Compliance Digest Newsletter
Subscribe to our DORA Digest newsletter and stay up to date with the key issues
and developments unfolding as the countdown to DORA continues.
ICT is now as essential to our daily lives as electricity. However, ICT has also created risks and vulnerabilities that expose financial entities – in particular – to an increasing number of cyber attacks or incidents. In 2019, the Boston Consulting Group pointed out that firms in the financial services industry were 300 times more likely than organisations in other sectors to be the target of cyber attacks. With increased levels of geopolitical instability worldwide since then, the threat has only become greater.
Despite the high threat level, ICT risks were addressed in a piecemeal fashion through various EU and national laws and not all sectors were covered equally.
With DORA, the EU aims to establish a universal framework for managing and mitigating ICT risk in the financial sector. By harmonising risk management rules across the EU, DORA seeks to remove the gaps, overlaps, and conflicts that could arise between disparate regulations in different EU states. A shared set of rules can make it easier for financial entities to comply, while improving the entire EU financial system's resilience by ensuring that every institution is held to the same standard.
Who is affected?
DORA has a broad scope and applies to more than 22,000 financial institutions and ICT service providers based in the EU, including (among others):
- banks;
- insurance companies and intermediaries;
- PSPs/EMIs;
- investment firms;
- pension funds;
- crypto-asset service providers;
- crowdfunding service providers;
- fund managers; and
- ICT third-party service providers.
The ICT infrastructure of all in-scope financial institutions will certainly be affected, but it will equally be relevant for ICT third-party service providers and existing contractual (outsourcing) arrangements with EU and non-EU counterparties.
Key requirements of DORA
DORA establishes technical requirements for financial entities and ICT providers across:
- ICT risk management;
- ICT incident reporting;
- digital operational resilience testing;
- ICT third-party risk management (TPRM); and
- information and intelligence sharing.
Requirements will be enforced proportionately, meaning that small and non-interconnected investment firms and payment institutions will have to comply with a simplified ICT risk management framework (which is described in the text of DORA itself).
- ICT risk management: DORA defines ‘governance’ as managing risks through each stage of their existence, from emergence to resolution, with an emphasis on the role of the senior management and board.
- ICT incident reporting: DORA standardises an ICT incident classification, notification and reporting framework for the collection, analysis, and escalation processes within financial entities.
- Digital operational resilience testing: DORA requires annual penetration testing (pentests) and/or periodic threat-led penetration testing.
- ICT third-party risk management: DORA requires firms to have a strategy for dealing with ICT third-party risk. It sets out more detailed guidance around the content of exit plans and substitutability assessments, as well as requirements for testing them.
- Information and intelligence sharing: This enables financial entities to set up arrangements among themselves so they can easily exchange cyber threat information, and processes for acting on the threat information received.
DORA timeline: From proposal to implementation
DORA compliance: Enforcement by supervisory authorities
After the 17 January 2025 deadline, enforcement will fall to designated regulators in each EU member state, known as the “competent authorities”. These authorities can enforce:
- Administrative fines for non-compliance: 2% of an organisation's total annual worldwide turnover, or up to 1% of the organisation's average daily turnover worldwide.
- Remedial measures to improve a financial institution’s operational resilience.
- Public reprimands of institutions that fail to comply with DORA’s requirements.
- Withdrawal of authorisation from financial institutions that consistently fail to comply with DORA.
- Orders for compensatory damages to the clients, customers or third parties of a financial institution that suffer a loss due to its DORA non-compliance.
“Lead overseers,” appointed by the competent authorities, will supervise ICT providers categorised as "critical". The lead overseers also have powers to enforce compliance.
The DORA compliance journey: The role of gap assessments
Most organisations that are in scope of DORA are likely to be at least partially in compliance with its requirements already. This means that, despite the full details of what DORA compliance entails not yet being in place, there is sufficient insight and guidance available for organisations to embark on their compliance journey.
At the heart of DORA is a need for financial organisations to manage cyber security risk appropriately. Experience shows that embedding, operating, and refining a complex process such as that required by DORA will take time. Organisations should start their preparations now, including a review of any steps they have already taken towards compliance.
A gap assessment is a critical part of this process. During the assessment, DORA’s requirements are measured against the organisation’s existing activities and operations. The result of the gap assessment will help to define the wider DORA compliance journey. In our experience, most organisations require a checklist that can be refined to reflect their existing practices – for example:
- Framework, policy, procedure and plans review process.
- Awareness and training for management teams and boards.
- ICT incident response plans and play books that cover (at a minimum) incident classification and reporting timelines.
- Coverage of ICT risk management frameworks in conjunction with ICT internal audit plans.
- ICT risk management framework, with coverage of a digital operational resilience strategy.
- Identification-related requirements within the existing ICT risk management framework.
- An approach to digital operational resilience testing.
- ICT third-party risk management for coverage of ICT concentration risk, ICT third-party inventory and contractual provisions.
These are high-level suggestions based on experience. We recommend performing a detailed gap assessment against all the requirements of DORA regulation, RTS and ITS.
We safeguard clients and their communities

Petroleum Development Oman Pension Fund
“Thomas Murray has been a very valuable partner in the selection process of our new custodian for Petroleum Development Oman Pension Fund.”

ATHEX
"Thomas Murray now plays a key role in helping us to detect and remediate issues in our security posture, and to quantify ATHEX's security performance to our directors and customers."

Northern Trust
“Thomas Murray provides Northern Trust with a range of RFP products, services and technology, delivering an efficient and cost-effective solution that frees our network managers up to focus on higher Value activities.”
Insights

Why 72 hours is the New Standard for M&A Cyber Due Diligence
A decade ago, cyber due diligence sat somewhere between “nice to have” and “we’ll deal with it post-close.” That world no longer exists.
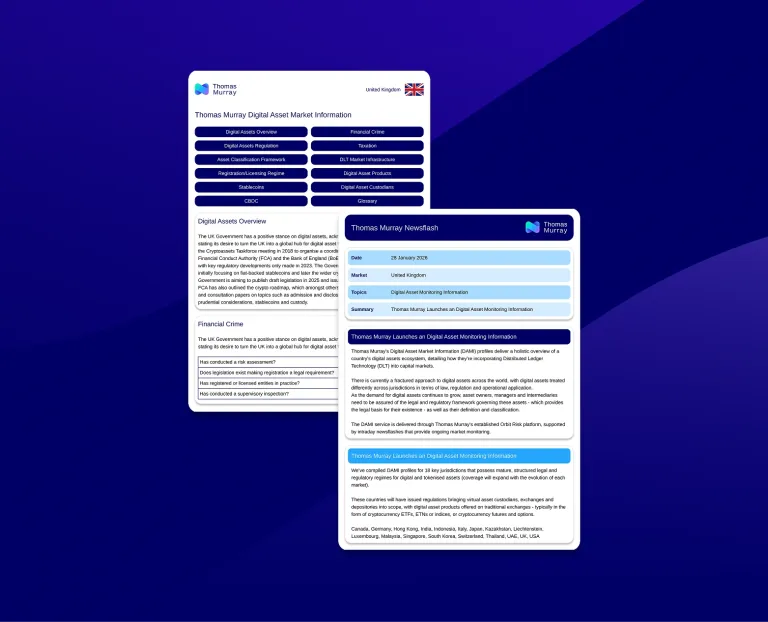
Thomas Murray Launches Digital Asset Market Information (DAMI)
Thomas Murray, a global leader in risk management, due diligence, and cybersecurity services, is proud to announce the launch of Digital Asset Market Information (DAMI).

Solving the "Scale Paradox": How to Automate Portfolio Oversight with Fewer People
In 2026, private equity technical teams are facing a "Scale Paradox": portfolios are growing in complexity, while in the internal teams responsible for operations and cybersecurity oversight, headcounts remain stagnant.

How Private Equity Hackers Choose Their Targets
Private equity firms sit at the intersection of high-value financial transactions, sensitive deal data, and an expanding portfolio of technology heavy portfolio companies – and it’s this combination that makes PE an attractive target for cyberthreat actors.

