Major ransomware attack disrupts London hospitals
In early June 2024, a significant ransomware attack targeted Synnovis, a provider of key pathology services to multiple NHS hospitals in London, including Guy’s Hospital, St Thomas’ Hospital, and King’s College Hospital. The attack caused widespread disruption and led to the declaration of a critical incident.
It forced the cancellation of non-emergency operations and blood tests, significantly impacting patient care and hospital operations (The Independent) (Enterprise Technology News and Analysis).

The ransomware attack has been attributed to the Qilin group, a Russian cyber gang known for its ransomware-as-a-service (RaaS) model. Synnovis’ IT systems were incapacitated, which had the effect of hindering critical pathology services and delaying urgent medical procedures like blood transfusions and transplants (The Independent) (BleepingComputer).

Efforts to mitigate the impact involved prioritising emergency cases, with non-urgent procedures postponed or redirected. As of writing, the National Cyber Security Centre (NCSC) and other cyber security bodies are actively involved in managing the response and investigating the incident (Enterprise Technology News and Analysis).
Major arrests in Scattered Spider cyber-crime group
In June 2024, law enforcement agencies made significant strides against the notorious Scattered Spider hacking group, with the arrest of key members. Spanish police, in collaboration with the FBI, apprehended Tyler Buchanan, a 22-year-old British national, at Palma de Mallorca airport while he was attempting to board a flight to Italy. Buchanan is suspected of being a prominent figure in the group, which has been linked to high-profile cyberattacks, including the breach of MGM Resorts International and multiple US companies (Krebs on Security).
Buchanan's arrest follows the earlier detention of another key member, Noah Michael Urban, in January 2024. Urban, a 19-year-old from Florida, faces charges related to wire fraud and identity theft. It is alleged that more than US$800,000 has been stolen through SIM-swapping and other cyber-crime activities (SiliconANGLE).
Scattered Spider, also known as Octo Tempest or UNC3944, is known for its sophisticated social engineering tactics, SIM-swapping, and collaboration with other ransomware groups like BlackCat/ALPHV. Their modus operandi includes phishing, exploiting multi-factor authentication (MFA) fatigue, and intimidating victims to gain access to sensitive data (BleepingComputer) .
These arrests will be a major blow to the gang – but these organisations are resilient and often quickly regroup. Despite the disruption, the collective knowledge and decentralised structure of cyber-crime communities mean that operations may continue, albeit at a temporarily reduced capacity.
LockBit ransomware group’s false Federal Reserve claim and website outage
In June 2024, the notorious LockBit ransomware group claimed to have breached the US Federal Reserve and boasted that it had stolen 33 terabytes of sensitive data. It threatened to release the stolen data unless its ransom demands were met within 48 hours. This bold assertion was prominently displayed on its Tor data leak site, and the group added pressure to its demands by criticising the current negotiator and requesting a replacement (Security Affairs) (The Daily Dot) .
However, cyber security experts quickly cast doubt on these claims. No sample data was released to verify the breach, and analysts – including those from vx-underground and Emsisoft – suggested that LockBit's statements were likely exaggerated or entirely fabricated to garner attention (The Daily Dot) (WinBuzzer).
Compounding the situation, LockBit's leak site experienced serious disruptions around the same time. This was part of an ongoing international law enforcement effort to dismantle the group's infrastructure. The takedown involved the collaboration of multiple agencies, which previously resulted in the seizure of numerous servers and cryptocurrency wallets linked to LockBit (Security Affairs) (TechWorm).
Also, it was revealed that the supposed Federal Reserve breach was a misidentification. LockBit had targeted another financial institution, not the Federal Reserve, further discrediting its initial claims and highlighting the group's increasing desperation in the face of intensified law enforcement actions (WinBuzzer) (TechWorm).
Thomas Murray cyber trends
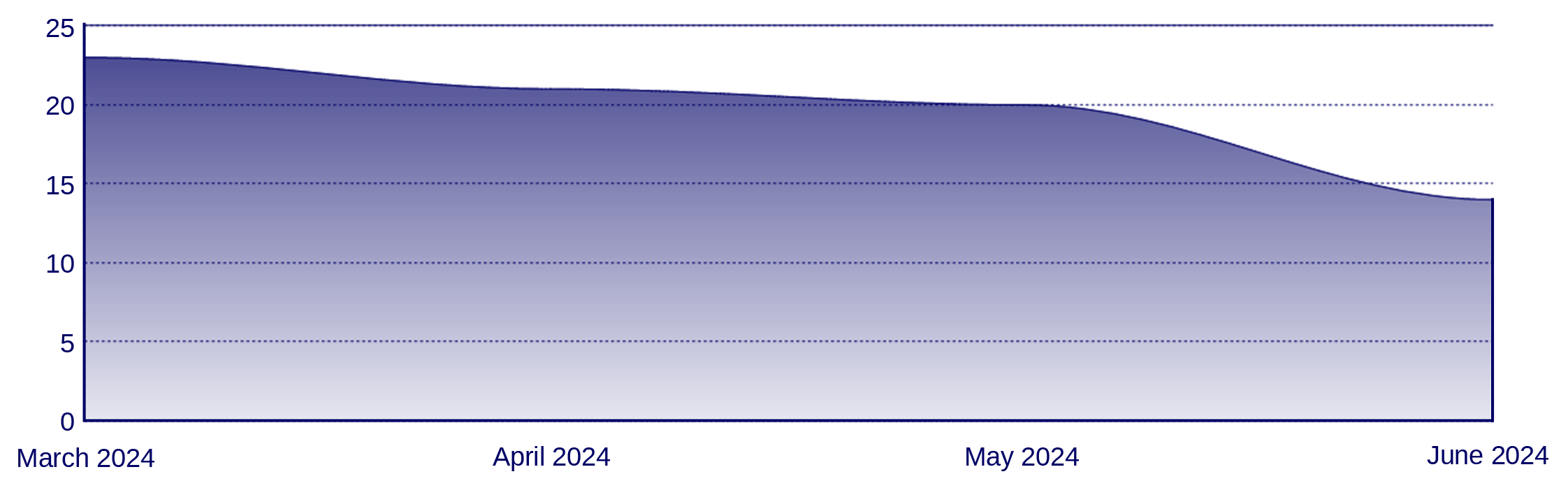
Ransomware vs Finance (last three months)
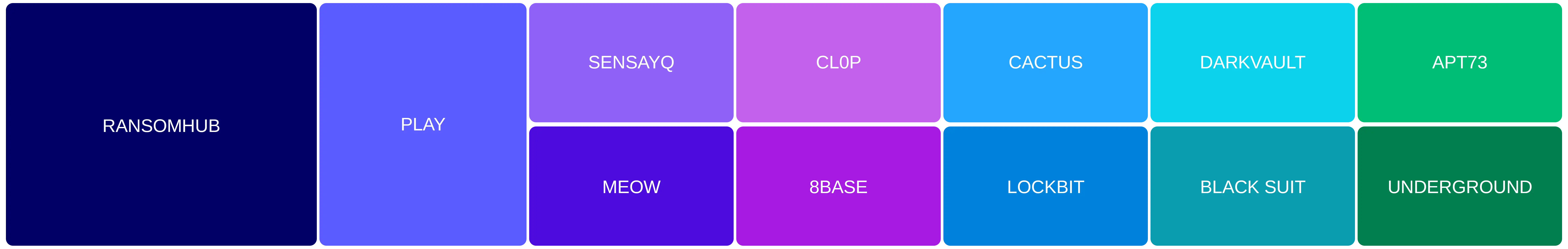
Ransomware groups targeting financial entities in June

Cyber Risk
We bring the best of our collective experience, energy and creative power to fiercely safeguard our clients and fortify their communities.
Insights

Ransomware at Europe’s Airports: Case for Community-Driven Third Party Risk Management
The recent ransomware attack on Collins Aerospace’s Muse software, which brought chaos to airports across Europe, serves as a stark reminder of a critical gap in how organisations approach Third Party Risk Management (TPRM).

JLR Cyber Attack: What it Means for Private Equity, Credit, and Equity Investments
From the iconic E-Type Jaguar to images of the late Queen driving modern Range Rovers on her estate, JLR has long held a uniquely British place in the national consciousness, even under Tata ownership. The incident has affected the owners of the business, the supply chain, and customers, and offers learnings for the Private Equity (PE) industry.

Impact of Cyber and Operational Resilience on Private Equity and Their Portfolio Companies
Implementing cyber and operational resilience measures is a strategic imperative for PE firms and their PortCos, enabling them to reduce the impact of cyber risks on asset valuations.

How Private Equity Leaders Turn Cyber Security Investment into Competitive Advantage
Leading firms are discovering something counterintuitive: investing in cyber security creates advantages worth far more than just protection.

