Legal woes for AT&T after massive data breach
AT&T revealed a significant data breach on 12 July, impacting around 110 million customers. The breach involved the unauthorised download of call and text records from its Snowflake cloud platform.
Although the breach did not include the content of communications or sensitive personal information like Social Security numbers, it exposed detailed interaction records, posing serious risks of phishing and fraud.
Reports have surfaced that AT&T allegedly paid a $370,000 ransom to the hacking group Shiny Hunters, which promised to delete the stolen data. This payment, reportedly verified by a security researcher, has sparked further debate on the ethics and effectiveness of paying ransoms. Despite the promise of deletion, experts caution that there is no guarantee the data is fully eradicated, and paying ransoms can perpetuate the cycle of cybercrime.


The breach has led to numerous class action lawsuits, including in Montana, New Jersey, and Texas. These legal actions highlight the potential financial and personal risks for affected customers. Moreover, the US Department of Justice’s involvement, citing national security concerns, underscores the severity of the incident. AT&T has responded by working closely with law enforcement to apprehend those responsible and by taking steps to secure their systems against future breaches. Legal action is becoming a common feature of the aftermath of cyber incidents.
AT&T has been proactive in addressing the breach, collaborating with law enforcement, and notifying affected customers. It has emphasised its commitment to protecting customer data and has provided resources to help customers safeguard their information. The breach has also prompted AT&T to review and enhance its cyber security measures to prevent similar incidents in the future.
Occurring in the same month as the global CrowdStrike/Microsoft outage, the AT&T breach serves as a stark reminder of the vulnerabilities inherent in cloud-based data storage and the critical need for robust cyber security protocols. It underscores the importance of transparency, prompt action, and continuous improvement in security practices.
For consumers, it highlights the necessity of vigilance in monitoring personal data and being aware of potential scams arising from such breaches (as we are seeing in the wake of the CrowdStrike incident). As the legal and regulatory landscapes evolve in response to such incidents, companies must prioritise robust security measures to protect their customers’ data and maintain their trust.
Fake CrowdStrike ‘fixes’ target companies with malware, data wipers
Threat actors moved swiftly to exploit the chaos caused by the widely reported global problems that followed a glitchy update from CrowdStrike, a prominent cyber security company, on Friday, 19 July.
Reports emerged of phishing campaigns targeting affected organisations, impersonating legitimate CrowdStrike communications. These phishing attempts designed to trick users into downloading malware under the guise of essential updates or fixes purportedly from CrowdStrike.
One notable malware campaign involved the distribution of a fake CrowdStrike Hotfix update, which, when installed, actually deployed the Remcos Remote Access Trojan (RAT) and other malicious payloads. Another attack saw threat actors distributing a data-wiping malware disguised as a CrowdStrike update, which effectively destroyed data on infected systems.
The pro-Iranian hacktivist group Handala claimed responsibility for impersonating CrowdStrike in phishing emails sent to Israeli companies. These emails contained links to malicious ZIP archives, purportedly containing necessary updates. Upon execution, these archives deployed the data-wiping malware, exacerbating the already significant disruptions caused by the original software glitch.
CrowdStrike has been actively assisting affected customers and advising them to verify communications through official channels to mitigate further risks from malicious actors. The company has since identified and corrected the root cause of the issue in its update process and continues to provide support to organisations still recovering from the fallout.
This incident underscores the critical need for organisations to maintain vigilant cyber security practices, including verifying communications, implementing timely security updates, and educating employees about phishing threats. Cyber security experts and affected parties alike remain focused on restoring operations and preventing future incidents of this magnitude.
Microsoft outage and the effect on the supply chain
CrowdStrike has now confirmed that the global Microsoft outage was due to a defect in its Falcon sensor software update, and not a cyberattack.
The company deployed a fix but acknowledged that manual intervention would be required to restore affected systems.
CrowdStrike has provided a workaround, advising affected customers to delete the faulty file in Safe Mode. The company is distributing a fixed version of the update via automatic channels. IT administrators and support teams initiated incident response plans, often involving manual interventions to bring systems back online. The recovery process is expected to take some time yet, with extensive efforts required to reboot systems and restore operations.
Financial markets reacted to the incident, with both CrowdStrike and Microsoft experiencing significant drops in their stock prices during premarket trading. This incident serves as a stark reminder of the complexities and risks inherent in modern IT environments and the need for comprehensive strategies to mitigate such vulnerabilities.
There will now be much discussion about the fragility of digital infrastructure and the critical need for resilience in IT and cyber security practices. Already, conversations are being had about the potential risks associated with vendors deploying wide-scale updates without sufficient oversight.
The outage underscored the importance of robust incident response plans and the need for vigilant management of software updates and IT infrastructure. Also, it brought attention to the interconnected nature of modern technology and the risks associated with concentration in the cloud services market, where only a few providers dominate. Ed Starkie, our Director of GRC, has emphasised the need for robust risk management and business continuity planning to deal with such events.
An unholy alliance: Global cyber experts on alert as hacktivist groups join Holy League
In an alarming development, the hacktivist groups Alixsec and NoName057 have merged under the newly formed Holy League, a coalition of numerous hacktivist entities.
Announced through a Telegram post by UserSec, this alliance includes prominent groups such as:
- High Society;
- UserSec;
- Cyber Army of Russia; and
- Anonymous Arabs.
This alliance – coming, as it does, amid the ongoing Russia-Ukraine and Israel-Palestine conflicts – signals a potential increase in sophisticated and coordinated cyber-attacks. These groups are known for their politically motivated cyber activities, so amplified attacks should be expected against NATO nations or those who are perceived to be allies of the groups’ enemies. Favoured targets will be critical infrastructure, government entities, and large corporations, necessitating robust cyber security measures and international cooperation to mitigate these threats.
Amplification attacks involve exploiting compromised devices or networks to inundate targets with overwhelming traffic, often crippling their services. The combined expertise and resources of the Holy League’s members are likely to result in more complex and powerful attacks. Such campaigns may involve distributed denial-of-service (DDoS) attacks, data breaches, and the spread of propaganda.
 |  |
Hacktivist group NullBulge claims to have breached Disney
Threat actors leak 1.1 TiB of internal Slack data, allegedly including messages, files, code, and more.
HackRead reports that a hacktivist group known as NullBulge says it has breached Disney's internal Slack infrastructure and leaked a massive amount of data, totaling 1.1 TiB (tebibyte) (approximately 1.2 TB [terabyte]).
The group, self-described as, “aiming to protect artists’ rights and ensure fair compensation for their work,” posted details of the alleged breach on the cybercrime platform Breach Forums on 12 July 2024.
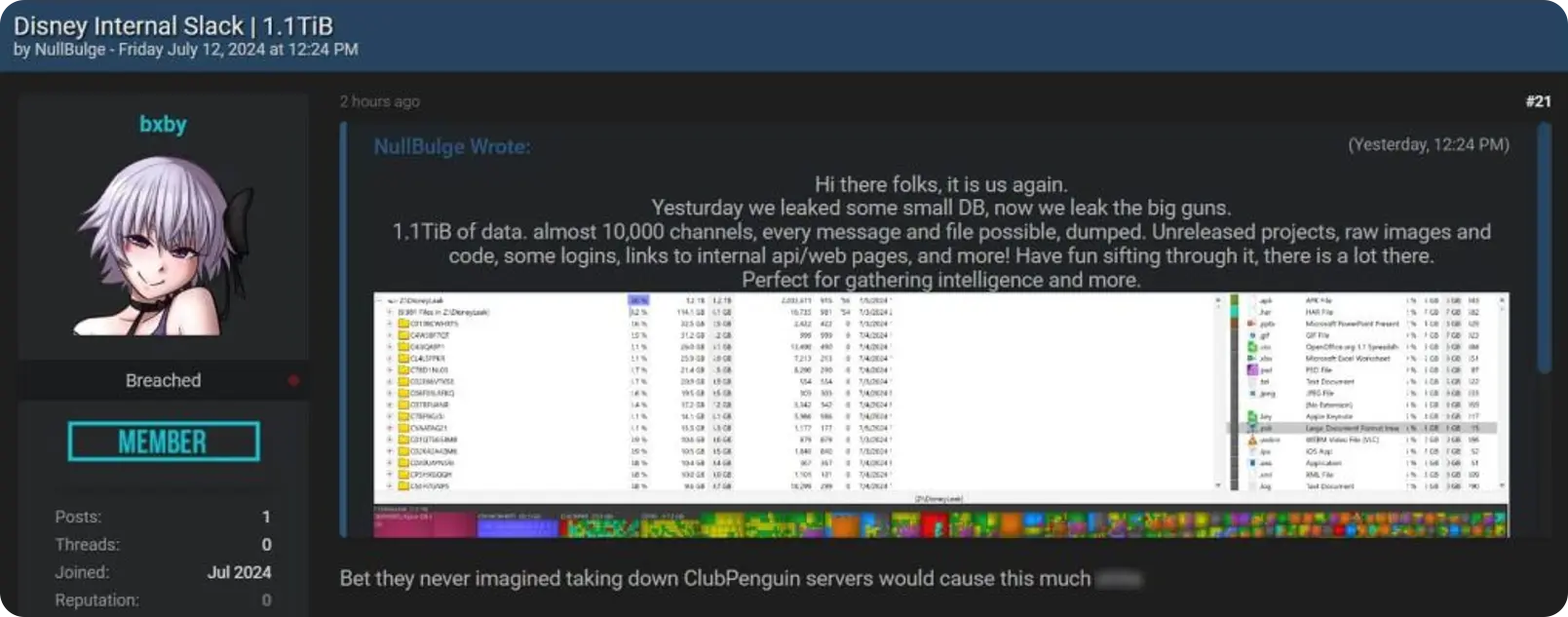
According to NullBulge, the leaked data includes a comprehensive copy of the Disney development team’s Slack communications. This encompasses messages, files, and other data exchanged on Slack. The hackers assert that the dump contains nearly 10,000 channels, including such sensitive information as:
- unreleased projects;
- raw images;
- code snippets;
- logins; and
- links to internal API/web pages.
NullBulge also publicised the breach on social media platform X, inviting others to explore the contents it claims to have obtained from Disney's internal communications.
NullBulge’s origins are so far obscure, though some experts suggest a potential link to the LockBit ransomware gang, based on the group’s use of tools associated with LockBit's leaked builder.
Disney has faced criticism and legal action over artist compensation, with notable figures like Neil Gaiman and Alan Dean Foster raising concerns about unpaid royalties for works tied to Disney-owned franchises such as Star Wars and Alien. Despite settlements in some high-profile cases, ongoing issues persist, prompting advocacy efforts from organisations like the Science Fiction and Fantasy Writers of America (SFWA).
As Disney investigates the reported breach, cyber security experts and affected parties await further developments to ascertain the authenticity and implications of NullBulge's claims.
ClickFix deception: A social engineering tactic to deploy malware
ClickFix is a social engineering tactic employed by threat actors to distribute malware through deceptive means.
It capitalises on exploiting human psychology and trust in seemingly legitimate notifications or error messages. Users are lured into clicking on these, unaware that they are downloading or installing malicious software onto their devices.
This tactic highlights the evolving sophistication of cyber threats, and the need for heightened user awareness and vigilance. Recognising and avoiding such schemes is crucial in protecting against cyber-attacks. It also underscores the importance of maintaining up-to-date security software and adopting best practices to mitigate the risks associated with social engineering tactics like ClickFix.
By understanding how ClickFix operates and staying informed about cyber security threats, individuals and organisations can better safeguard their digital environments against malicious activities aimed at compromising sensitive information and systems.
This tactic begins with users being redirected from compromised websites to domains with fake pop-up windows, instructing them to paste a script into a PowerShell terminal. This social engineering approach uses the appearance of authenticity to deceive users into executing malicious scripts.
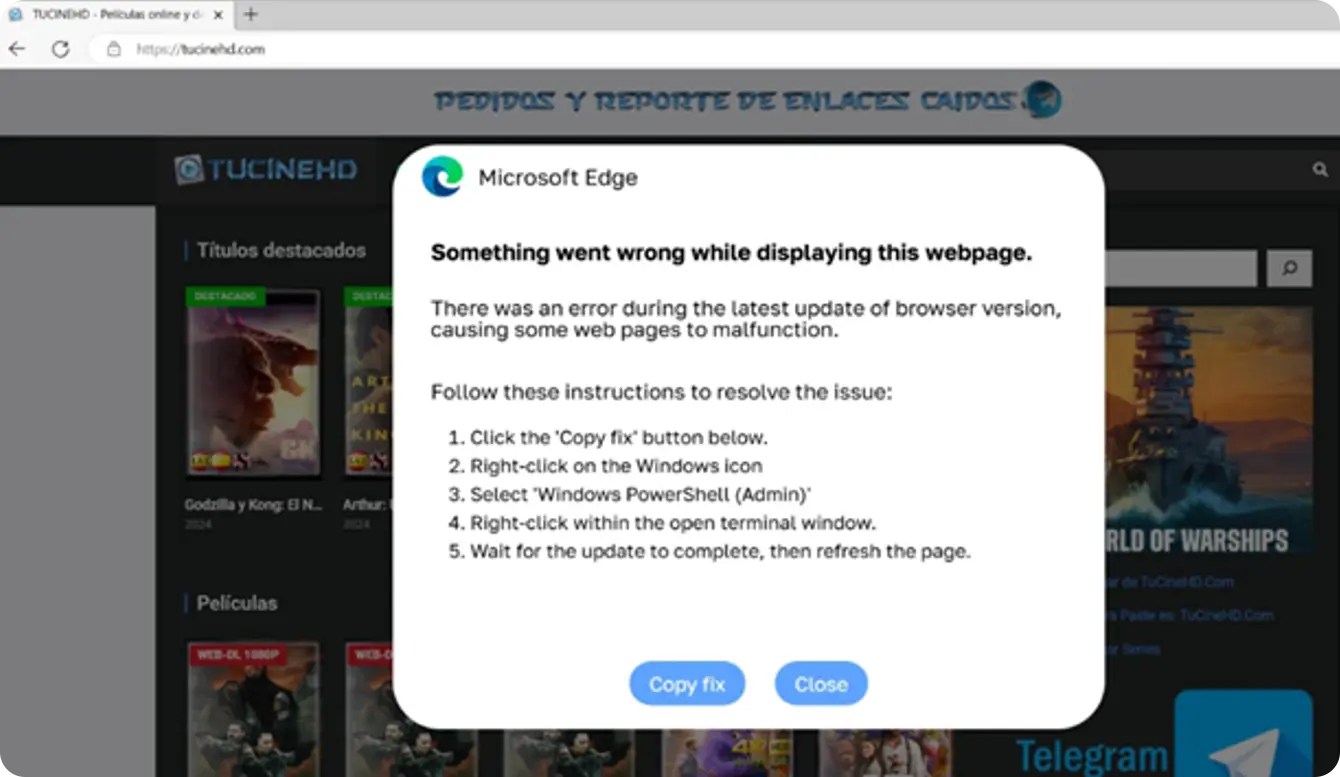
Key details
1. Mechanism
- Users visit seemingly legitimate but compromised websites.
- They are redirected to fake pop-ups prompting them to paste scripts into PowerShell.
- Executing these scripts allows malware to infiltrate systems, leading to potential data theft and system compromise.
2. Examples of malware
- DarkGate: Steals sensitive information, provides remote access, and establishes persistent backdoors.
- Lumma Stealer: Uses error prompts to trick users into executing malicious PowerShell scripts.
3. Technical analysis
- The scripts are often base64-encoded and contain commands to download and execute HTA files from remote servers.
- JavaScript snippets manage the interactions and clipboard contents to ensure the malicious script is executed.
- Once executed, these scripts perform various harmful actions, such as creating folders, dropping executables, and communicating with C2 servers.
4.Social engineering tactics
- Phishing emails with HTML attachments disguised as Word documents.
- Fake error messages instructing users to execute scripts to fix supposed issues.
Cisco warns of critical flaw affecting Smart Software Manager On-Prem
Cisco has issued urgent patches to address critical vulnerabilities affecting its Smart Software Manager On-Prem (Cisco SSM On-Prem) and Secure Email Gateway (SEG) systems.
The most severe flaw, tracked as CVE-2024-20419 with a CVSS score of 10.0, allows remote, unauthenticated attackers to change the password of any user, including administrators, by exploiting flaws in the password-change process. This vulnerability impacts Cisco SSM On-Prem versions 8-202206 and earlier, but has been remedied in version 8-202212; version 9 remains unaffected.
Additionally, Cisco addressed another critical flaw (CVE-2024-20401, CVSS score: 9.8) in its Secure Email Gateway. This vulnerability permits attackers to add users with root privileges and cause permanent denial-of-service conditions by sending emails with malicious attachments.
In response to these vulnerabilities, the US Cybersecurity and Infrastructure Security Agency (CISA) has added three additional vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalogue. These include:
- CVE-2024-34102, affecting Adobe Commerce and Magento Open Source;
- CVE-2024-28995, impacting SolarWinds Serv-U; and
- CVE-2022-22948 affecting VMware vCenter Server.
Of these, CVE-2024-34102 (CosmicSting) is particularly severe, allowing attackers to execute remote code due to improper handling of nested deserialisation, with a proof-of-concept exploit already circulating.
CISA mandates federal agencies to apply vendor-provided mitigations for these vulnerabilities by 7 August 2024, to secure their networks against active threats. Cisco advises all affected users to promptly apply the necessary updates and follow recommended security practices to mitigate the risks posed by these vulnerabilities.
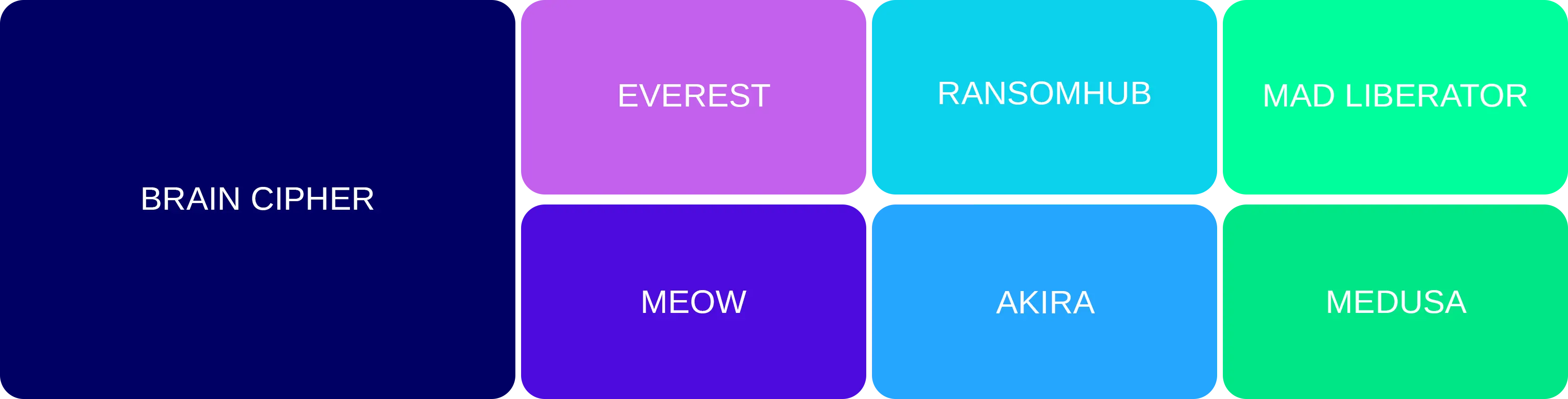
Ransomware groups targeting financial entities in July
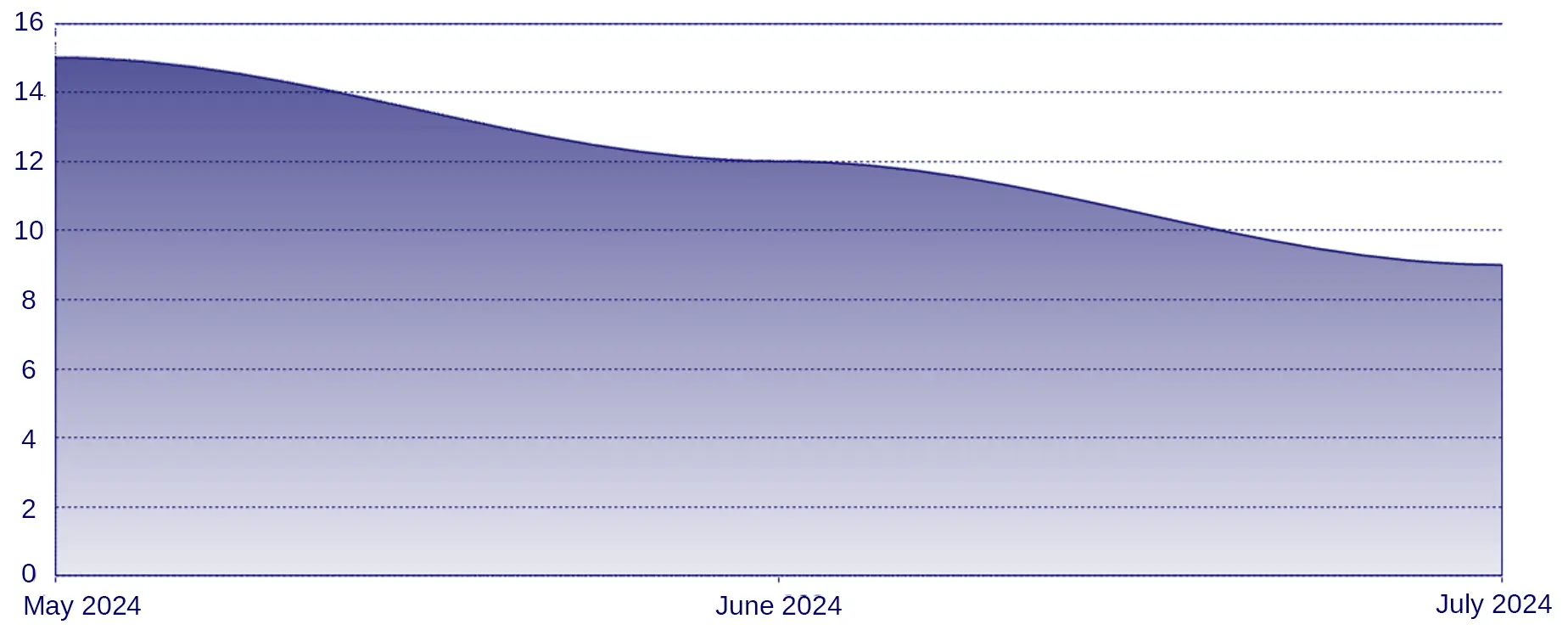
Ransomware vs Finance (last three months)

Cyber Risk
We bring the best of our collective experience, energy and creative power to fiercely safeguard our clients and fortify their communities.

Thomas Murray cyber alerts
Subscribe to stay up to date with developing threats in the cyber landscape
Insights

Ransomware at Europe’s Airports: Case for Community-Driven Third Party Risk Management
The recent ransomware attack on Collins Aerospace’s Muse software, which brought chaos to airports across Europe, serves as a stark reminder of a critical gap in how organisations approach Third Party Risk Management (TPRM).

JLR Cyber Attack: What it Means for Private Equity, Credit, and Equity Investments
From the iconic E-Type Jaguar to images of the late Queen driving modern Range Rovers on her estate, JLR has long held a uniquely British place in the national consciousness, even under Tata ownership. The incident has affected the owners of the business, the supply chain, and customers, and offers learnings for the Private Equity (PE) industry.

Impact of Cyber and Operational Resilience on Private Equity and Their Portfolio Companies
Implementing cyber and operational resilience measures is a strategic imperative for PE firms and their PortCos, enabling them to reduce the impact of cyber risks on asset valuations.

How Private Equity Leaders Turn Cyber Security Investment into Competitive Advantage
Leading firms are discovering something counterintuitive: investing in cyber security creates advantages worth far more than just protection.

