Our Cyber Advisory team has been monitoring a spike in DDoS attacks on the financial sector that can often be linked to geopolitical events. The current conflicts in Ukraine and Palestine have created an overlap of ideals and agendas between various hacktivist groups (i.e. ideologically motivated cyber crime gangs).
Although these groups may have different objectives, some are collaborating with each other. Their weapon of choice is the distributed denial of service (DDoS) attack. DDoS attacks have long been an issue for the banking and financial sector, and now the number of these attacks is increasing. Threat actors are intent on causing economic damage – not just to their targeted organisations, but to the wider populations they serve.

More intelligence about DDoS
On 17 January, our threat intelligence lead held an exclusive broadcast for our clients to update them on what this latest spike in DDoS threats means and what they can do to better protect themselves. We produced a whitepaper to accompany this presentation that is available on request.
Distributed denial of service
A denial of service (DoS) attack aims to overload a computer system or network with traffic, making it unavailable to its intended users. A DDoS attack is the more sophisticated version of a DoS attack – DDoS attacks are harder to prevent, because they use multiple coordinated devices to flood the targeted service. Typically, a network of compromised computers (i.e. a botnet) is used to conduct a DDoS attack.
DDoS attacks are typically short-lived; however, an overloaded server can cause significant downtime that affects services for extended periods. Typically, DDoS attacks target customer landing sites, login pages and application programming interfaces (API) because they have a significant impact on the user base.
Not only are DDoS attacks hard to prevent, but they can also:
- cause significant reputational damage;
- harm search engine optimisation (SEO) – meaning that a website becomes less visible to search engines like Google; and
- create recovery costs.
DDoS attacks may also be used as a distraction for other, more damaging attacks (such as ransomware). This highlights the need for meticulous planning and testing of DDoS incident responses.
Graph 1: Total number of daily DDoS attacks across a range of groups tracked by Thomas Murray
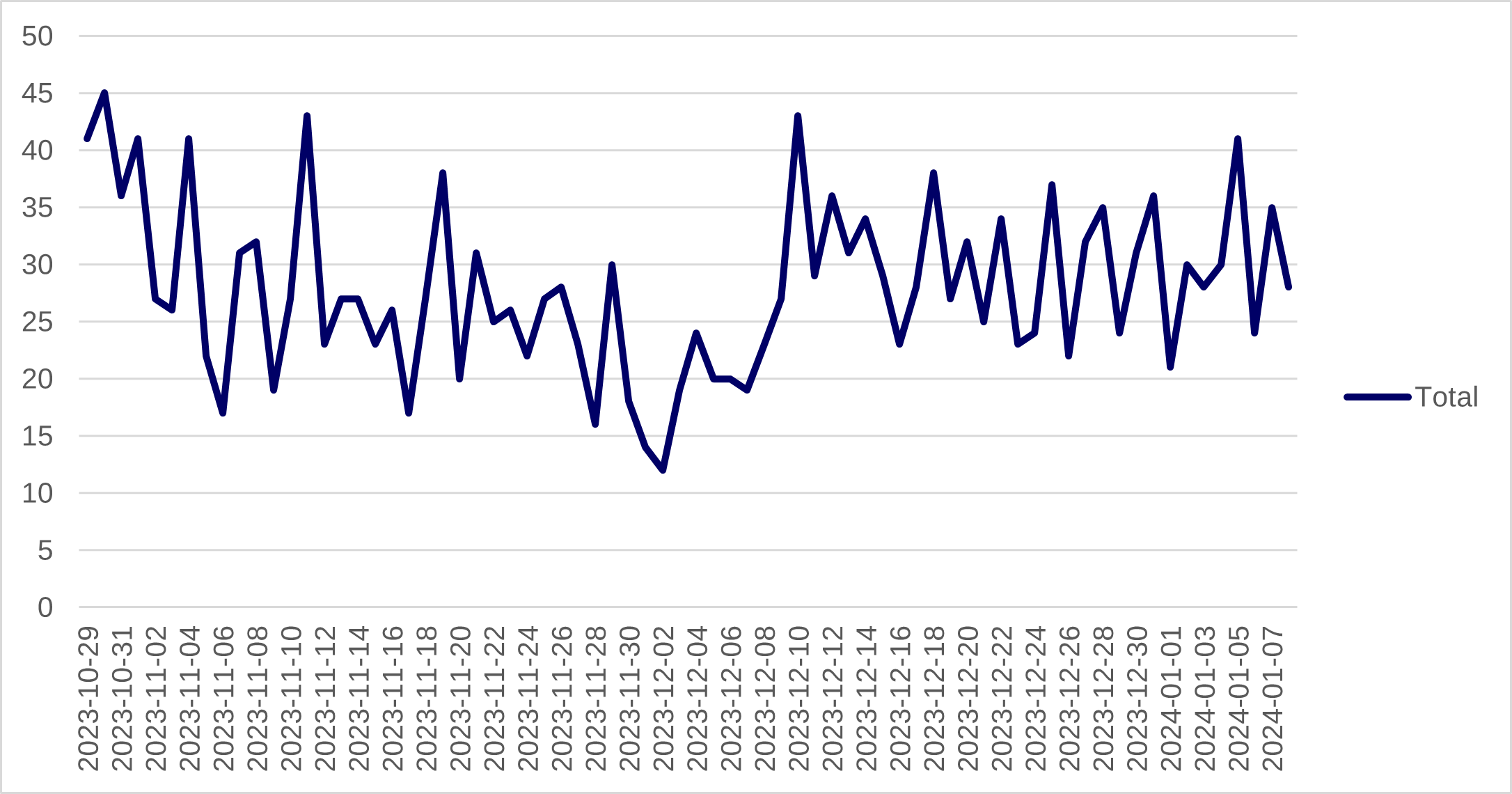
Government offices/agencies make for favoured targets, as hacktivists view disrupting their operations as key to bringing their political agendas and ideologies to public attention. Logistical hubs, on the other hand, make for prime targets because supply chain disruption causes high levels of economic loss and can create chaos.
The banking and financial sector is also becoming an increasingly important target for hacktivist groups.
Why banks?
After the initial invasion of Ukraine on 12 March 2022, SWIFT disconnected seven Russian banks to comply with EU Council Regulation 2022/345. Pro-Russian hacktivist groups have attacked banks in Europe or NATO-aligned nations and made direct reference to this decision in their public posts. The aim is to make the population of these target states experience the same levels of frustration and inconvenience as Russian nationals.
Banks tend to have large user bases, so targeting them can cause significant disruption. The hope is that the affected users will become disillusioned with their country’s support of Ukraine. Although downtime is usually minimal, operational delays can be serious.
A strict regulatory environment applies further pressure to banks, and threat actors play on their fears of fines and reputational damage. Furthermore, interrupting services could make the country’s financial infrastructure appear unstable, with implications for the wider economy.
Successful attacks against central and global banks burnish an adversary’s reputation and highlight their capabilities. The adversary will show off their ability publicly, and these sorts of attacks often make the news and local media. This attention helps spread the adversary’s political aims and ideology.
February 2023 was a key turning point; Anonymous Sudan began targeting Swedish and Danish entities before joining pro-Russian groups in switching its focus to other NATO-aligned targets. It is also important to note that these groups also have a declared collaboration with members of the former ransomware gang REvil.
Based on both the profiles of those targeted and Thomas Murray’s analysis of the posts made by adversaries in which they explicitly state why they are choosing specific targets, figure 1 shows those entities most at risk from sustained DDoS attacks.
Targets are chosen based on their perceived geopolitical alignment, even though this may not be accurate. What matters is the adversary’s perception of the target’s sympathies.
Figure 1: Who is at risk?
.webp)
Summary
Hacktivist groups have already promised further attacks on banks and the wider financial industry. This is, in part, because of the widespread economic and humanitarian impact of the sanctions on Russia. These threats, when coupled with the data collected by Thomas Murray, are evidence that 2024 will be an especially difficult year for the global financial sector when it comes to fending off cyber-attacks.
Recommendations
- Understand your organisation’s attack surface. This will help protect against adversaries exploiting its vulnerabilities. Thomas Murray’s Orbit Risk can assist with continuously monitoring both your organisation and your third parties for real-time and emerging risks.
- Consider DDoS protections, such as implementing load balancers and content distribution networks, along with next-web application firewalls.
- Develop an incident response and recovery plan. Ensure that this is tested and maintained to ensure all contact information is up-to-date.
- Implement multifactor authentication (MFA) and the principle of least privilege to reduce the risk of unauthorised access.
- Conduct penetration testing of your network and use specific threat-hunting services.
- Run network and endpoint monitoring.
Questions to ask your organisation

Cyber Risk
We bring the best of our collective experience, energy and creative power to fiercely safeguard our clients and fortify their communities.
We safeguard clients and their communities

Petroleum Development Oman Pension Fund
“Thomas Murray has been a very valuable partner in the selection process of our new custodian for Petroleum Development Oman Pension Fund.”

ATHEX
"Thomas Murray now plays a key role in helping us to detect and remediate issues in our security posture, and to quantify ATHEX's security performance to our directors and customers."

Northern Trust
“Thomas Murray provides Northern Trust with a range of RFP products, services and technology, delivering an efficient and cost-effective solution that frees our network managers up to focus on higher Value activities.”
Insights

Ransomware at Europe’s Airports: Case for Community-Driven Third Party Risk Management
The recent ransomware attack on Collins Aerospace’s Muse software, which brought chaos to airports across Europe, serves as a stark reminder of a critical gap in how organisations approach Third Party Risk Management (TPRM).

JLR Cyber Attack: What it Means for Private Equity, Credit, and Equity Investments
From the iconic E-Type Jaguar to images of the late Queen driving modern Range Rovers on her estate, JLR has long held a uniquely British place in the national consciousness, even under Tata ownership. The incident has affected the owners of the business, the supply chain, and customers, and offers learnings for the Private Equity (PE) industry.

Impact of Cyber and Operational Resilience on Private Equity and Their Portfolio Companies
Implementing cyber and operational resilience measures is a strategic imperative for PE firms and their PortCos, enabling them to reduce the impact of cyber risks on asset valuations.

How Private Equity Leaders Turn Cyber Security Investment into Competitive Advantage
Leading firms are discovering something counterintuitive: investing in cyber security creates advantages worth far more than just protection.

