The EU’s Digital Operational Resilience Act (DORA) will apply from 17 January 2025. It applies to a wide range of financial entities, including alternative investment fund managers (AIFMs). Private equity firms that are authorised AIFMs will be subject to DORA, but sub-threshold AIFMs are exempt.
For Luxembourg entities, compliance may be assessed by the Commission de Surveillance du Secteur Financier (CSSF) or other appointed authorities.
Private equity firms will be subject to DORA due diligence, as well as needing to conduct DORA due diligence on investment companies and counterparties.


Firms that have not already started preparing for DORA still have a small window in which to achieve compliance. Even those firms that are not affected by DORA can use the regulation to maximise their operational resilience and strengthen their cyber security posture.
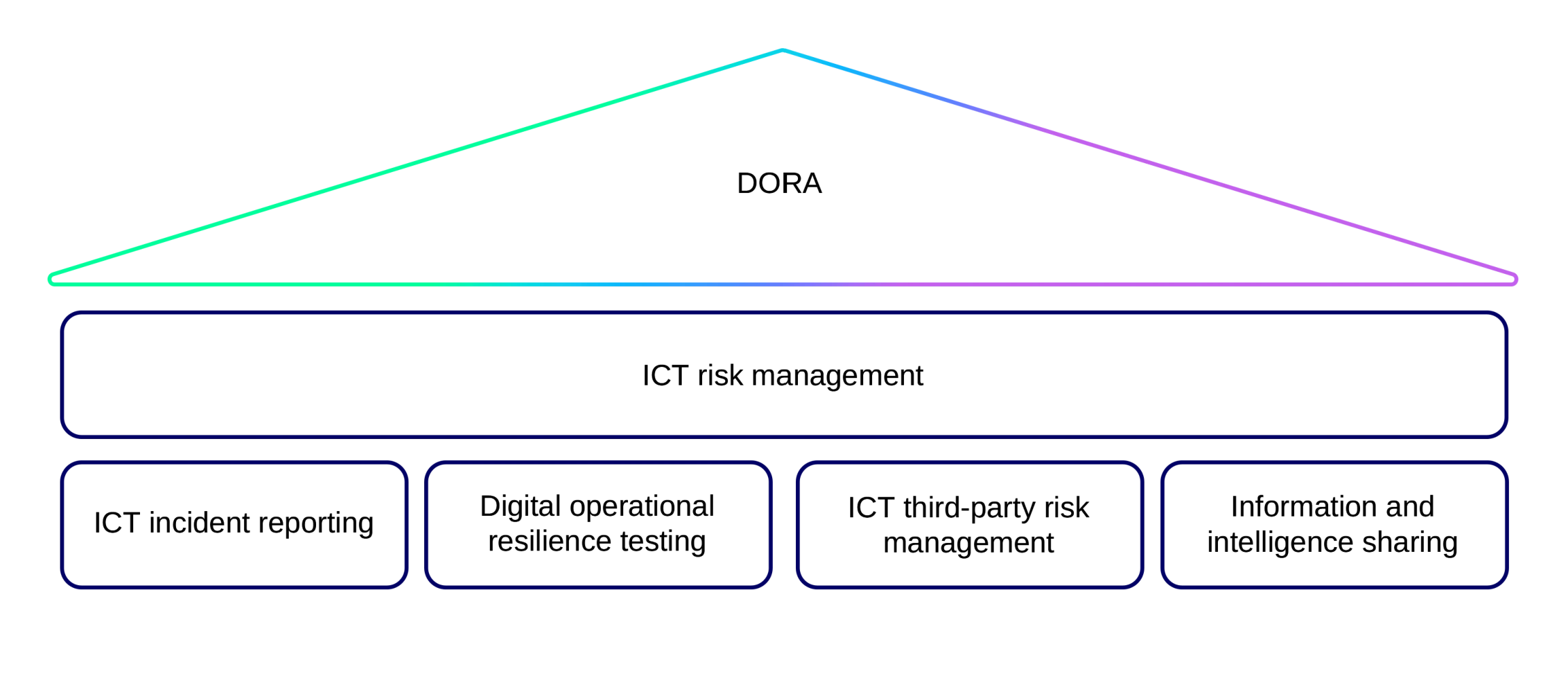
(or main areas) that private equity firms will need to address now, if they haven’t already:
- Information and communication technology (ICT) risk management
- ICT-related incident management, classification and reporting
- Digital operational resilience testing
- Management of ICT third-party risk
- Information sharing arrangements
Firms should start by identifying and mapping ICT systems/providers, reviewing policies and procedures, assessing current capabilities vs. requirements, and developing an implementation roadmap.
Unlike other regulations in this space that have been seen before, DORA makes technology, resiliency and the management of technology risk a true board-level issue. DORA requires establishing an internal governance and control framework for ICT risk management. The board/senior management will be responsible for defining, approving and overseeing the implementation of ICT risk management.
There are new requirements for contractual provisions with ICT service providers and obligations in case of breaches by providers. DORA does, however, recognise that requirements should be implemented proportionally based on a firm's size, risk profile, and complexity.
Changing the relationship between vendors and firms
DORA will have a huge impact on the relationship between private equity firms and their third-party providers. Private equity firm leadership will be required to engage with third-party provider risk at a level that has not been seen before. Board members must be kept informed of technology risk on an ongoing basis, with appropriate educational support for them to ensure the management of technology risk is informed. Gone are the days of leaving IT and technology to an individual in the back office – IT risk is now a permanent item on the board’s agenda.
Enhanced due diligence
Private equity firms must conduct more thorough assessments of their ICT service providers' security posture, risk management practices, and DORA compliance. This includes evaluating the technology and systems used by vendors, not just internal systems. Having an in-depth understanding of the technology that is used to support business operations is fundamental to achieving compliance.
Contractual requirements
Contracts with ICT service providers need to be updated to include specific DORA compliance clauses. These should cover:
- Incident reporting procedures
- Information sharing protocols
- Audit rights
- Exit strategies
Ongoing monitoring
Firms are required to continuously monitor their service providers' adherence to DORA requirements. This may involve:
- Regular reviews of services against established (and meaningful) KPIs.
- Audits and external validation activities that demonstrate compliance to DORA.
Critical provider designation
DORA introduces the concept of “critical ICT third-party service providers,” which will be subject to direct regulatory oversight. Private equity firms need to identify which of their providers may fall into this category.
Risk management strategy
Firms must establish a comprehensive strategy for managing third-party risks and maintain a register of agreements with ICT service providers.
Subcontractor oversight
Private equity firms need to extend their due diligence to include service providers’ subcontracting arrangements, often referred to as either ‘fourth party’ or ‘Nth party’ relationships.
Exit planning
Only 17% of firms currently have exit strategies in place for critical vendors. DORA requires the development of both ‘soft’ and ‘hard’ exit strategies for key providers.
Information sharing
There’s an increased emphasis on sharing threat intelligence within trusted communities, which may involve third-party providers.
Operational burden
The additional requirements are likely to increase the operational resources needed to manage third-party relationships effectively.
Private equity firms will need to develop closer, more transparent relationships with their ICT service providers to ensure mutual compliance and enhanced operational resilience.
If you are struggling with your cyber security and data protection, or need help with DORA compliance, at Thomas Murray we are uniquely placed to help you. We offer bleeding edge cyber security guided by threat intelligence, regulatory expertise, and years of experience in assisting funds of all kinds. Talk to us today to find out more about what we can do for you.
Free Private Equity Portfolio Cyber Risk Assessment
Identify high-risk issues across your portfolio companies, receive contextual threat intelligence to answer the “so what”, and more importantly what steps should you take to reduce the risk.


Orbit Risk
Achieve trust, transparency and security with a single platform. A leading solution for companies looking to digitise and automate their risk management, leveraging Intelligence, Diligence and Security.
Insights

NYSE proposes around-the-clock trading
The New York Stock Exchange exploring the possibility of trading on a 24/7 basis has caused both excitement and concern among market participants.

Cash correspondent banking and monitoring: A primer
Correspondent banking, whether traditional or digital, plays a vital role in the international financial system.

Correspondent monitoring: A safeguard against the worst-case scenario
Correspondent banking plays a vital role in the global financial system, though it does carry significant risks.

Liquidity in Ghana and Zambia
The state of foreign exchange liquidity across Africa often shares several key features and challenges that impact the region’s financial markets.


